A Student-Run Pentest: CCSO X HAX
As one of my last projects before graduating from Penn State this past Spring, I worked with Jonathan Skeete and other members of Penn State’s Competitive Cyber Security Organization to organize an entirely student-run penetration test of the HAX CMS Web Application. We worked over the course of 5 weeks to perform static analysis and dynamic testing of HAX to uncover vulnerabilities, and delivered a comprehensive final report detailing our findings.
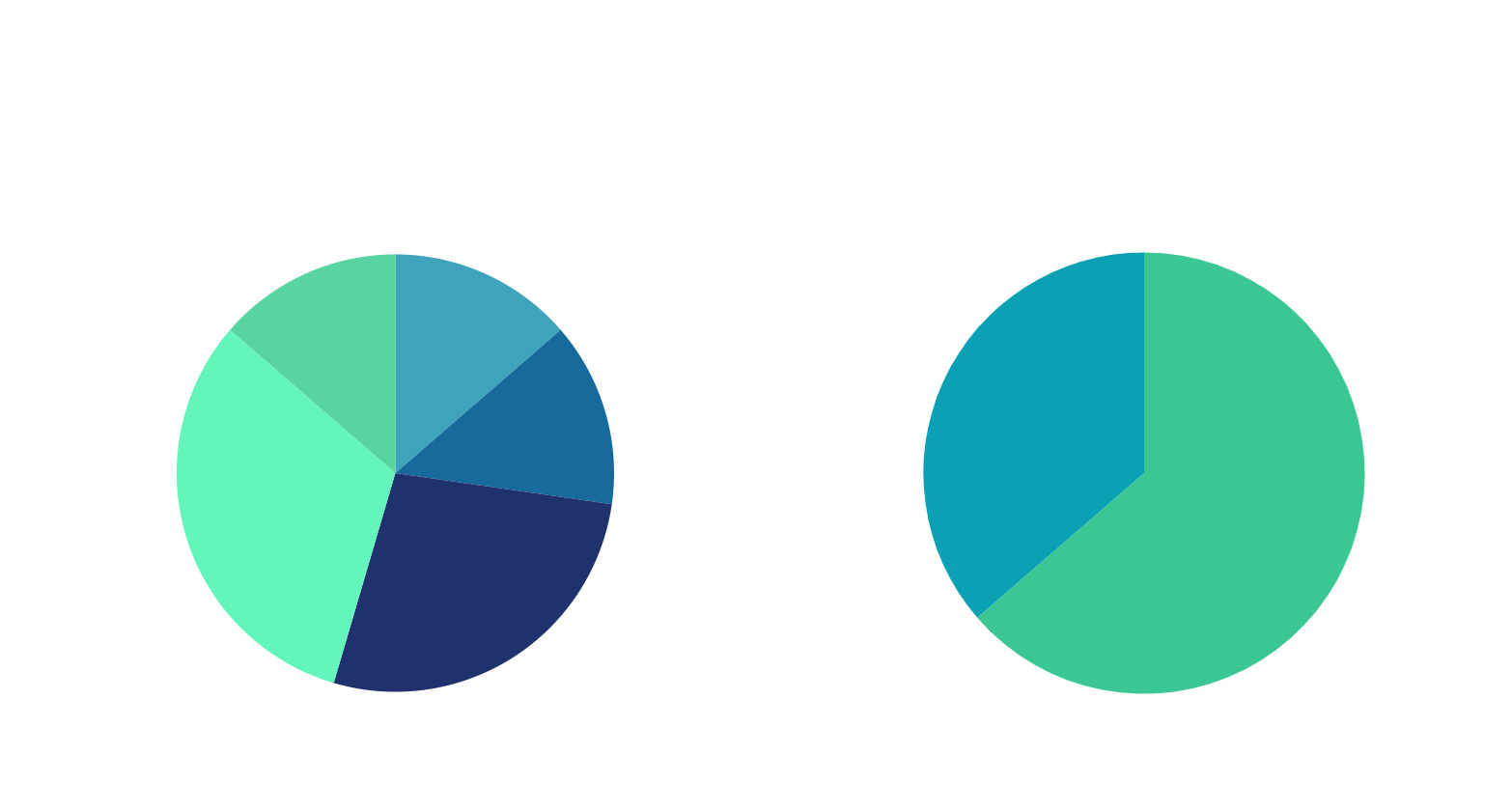
During the engagement we identified 22 vulnerabilities, 14 of which went on to become published CVEs! I had so much fun getting to run this project, it was really amazing to have an opportunity for students to gain hands on experience testing webapps, and to contribute to the security of a Penn State project making the web a better place.
I’m also particularly proud to share that this resulted in the publishing of my first 7 CVEs (RAHHHHHHHHHHHH):
| Vulnerability | CVE | Links |
|---|---|---|
| Lack of Authz Checks | CVE-2025-54378 | GitHub Advisory, NVD |
| User Enumeration | CVE-2025-54129 | GitHub Advisory, NVD |
| Default Credentials | CVE-2025-54137 | GitHub Advisory, NVD |
| Clickjacking | CVE-2025-54139 | GitHub Advisory, NVD |
| Improper Session Termination | CVE-2025-53642 | GitHub Advisory, NVD |
| Stored Cross-Site Scripting | CVE-2025-49137 | GitHub Advisory, NVD |
| Iframe Phishing / Unrestricted Iframe Content | CVE-2025-49139 | GitHub Advisory, NVD |
What’s HAX?
HAX is a ubiquitous web publishing platform developed at Penn State by Bryan Ollendyke and his collaborators (the HAX Lab). It’s a CMS and static site generator designed to allow anyone to easily create and publish websites that are fast and easy to maintain without having any understanding of the underlying technologies.
The project is fully open source, and has a handful of different components. The base HAX CMS is a single-user deployment that allows for the creation of different websites based on themes and webcomponents. Each website that you create in the HAX editor is represented under the hood by a JSON schema that details the content of the site allowing for sites to be stored and created quickly without a database. There’s both a NodeJS and a PHP version of the CMS which are developed in parallel.
To supplement this, HAXiam serves as a wrapper for the CMS allowing for multi-user deployments. It allows for integration with SSO and for multiple users to create and deploy their own HAX sites. The resulting sites can be either hosted by the CMS, or deployed to another platform.
All of this left us with a lot of interesting areas to target during testing. Going into it I was most interested with the multi-user functionality, and the CMS itself as opposed to the static sites or the generation process.
The Test
The goal of this test was to get Penn State students real hands-on experience conducting a penetration test while contributing to the overall security of the HAX project. All the students involved got to experience planning & scoping, working with a client, conducting a pentest, and writing & delivering a report.
Planning
Before conducting the test, we worked with Penn State’s Office of Information Security to get authorization to perform the work. We collaborated with Bryan to create a scope and draft a Statement Of Work (SOW) outlining the timeline and rules of engagement for the test, and to get a testing environment provisioned.

We put together a group of 14 students with varying skill levels to conduct the pentest. Our team included members of our Collegiate Penetration Testing Team (CPTC), as well as both newer club members and graduating seniors looking to gain more hands-on experience. We planned to conduct the test mostly in pairs, allowing less experienced team members to work with and learn from the CPTC team and more seasoned members.
Testing
We held biweekly sessions for five weeks to perform the HAX test, and to work on our final report. We began by holding a kickoff meeting with the client (Bryan) to have him explain the application to the larger group, identify any areas of concern, and reinforce the rules of engagement.
Afterwards we started off with static analysis and familiarizing ourselves with the application. We walked through all the functions of the app to understand both the web requests involved and the underlying code associated with actions such as creating/modifying a site, logging in, and uploading files.
Once we had a handle on how everything worked we pivoted to dynamic testing of our identified points of interest. We tested for logic issues and design flaws as well as common vulnerabilities such as cross-site scripting (XSS), command injection, and authentication/authorization issues. Having ready access to both the source code and the application’s developer(s) made this test 10x easier as we were able to craft potential exploits based on the application’s code and talk through potential issues with Bryan.
The Findings
Our team ended up with a total of 22 findings broken down as follows:
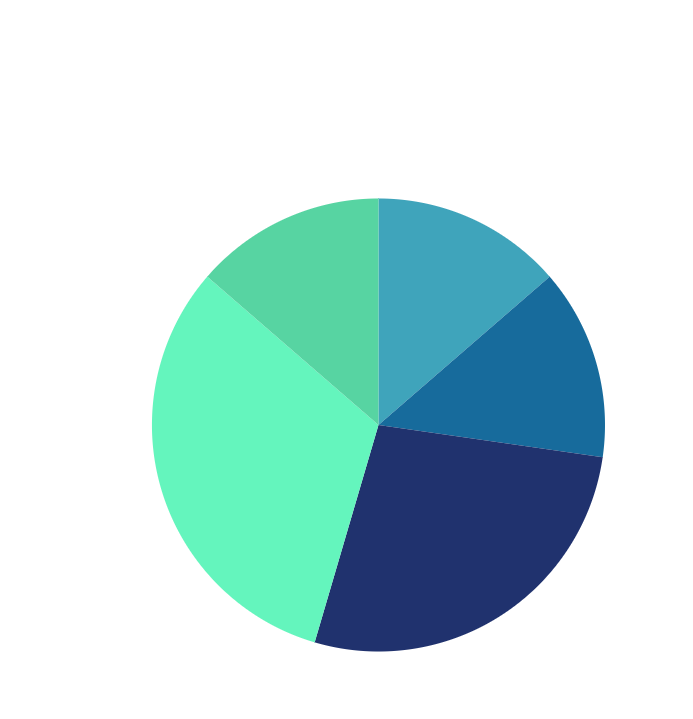
Our most critical findings allowed for authenticated remote code execution (RCE) on the underlying HAX server, and for the unauthorized modification and defacement of other user’s sites. Additionally we were able to identify both stored and self XSS, user enumeration, LFI, and other vulnerabilities that included insecure design choices.
After the test, we compiled a 57 page report detailing our findings and recommendations for Bryan and his team to tackle. We included detailed breakdowns of each vulnerability, remediation steps based on the source code, and explanations of how an attacker could use each vulnerability.
Here’s a full list of our findings which were published as GitHub Advisories and CVEs after the test concluded:
| Vulnerability | CVE | Links |
|---|---|---|
| RCE via Insecure File Upload | CVE-2025-32028 | GitHub Advisory, NVD |
| Command Injection | CVE-2025-49141 | GitHub Advisory, NVD |
| Improper Error Handling (DOS) | CVE-2025-54134 | GitHub Advisory, NVD |
| Information Disclosure | CVE-2025-48996 | GitHub Advisory, NVD |
| Insecure Default Configuration (Lack of AuthN) | CVE-2025-54127 | GitHub Advisory, NVD |
| Disabled CSP | CVE-2025-54128 | GitHub Advisory, NVD |
| LFI | CVE-2025-49138 | GitHub Advisory, NVD |
| Lack of Authz Checks | CVE-2025-54378 | GitHub Advisory, NVD |
| User Enumeration | CVE-2025-54129 | GitHub Advisory, NVD |
| Default Credentials | CVE-2025-54137 | GitHub Advisory, NVD |
| Clickjacking | CVE-2025-54139 | GitHub Advisory, NVD |
| Improper Session Termination | CVE-2025-53642 | GitHub Advisory, NVD |
| Stored Cross-Site Scripting | CVE-2025-49137 | GitHub Advisory, NVD |
| Iframe Phishing / Unrestricted Iframe Content | CVE-2025-49139 | GitHub Advisory, NVD |
If you’re interested in reading more about the vulnerabilities themselves, each GitHub Advisory has a full breakdown of the attack path.
The Aftermath

After the test we had a meeting with Bryan to walk through all of our findings, discuss potential fixes, and outline our next steps. We used this opportunity to get feedback on the report and identify any areas that needed additional clarification to allow the HAX team to properly patch the vulnerabilities.
In the weeks after the test had concluded and we had issued our report we continued to communicate with Bryan to collaborate on remediations, retesting where needed, and the status of patches. We also issued GitHub Security Advsiories for each of our applicable findings to communicate them to HAX users, allow for tracking, and to formalize them as CVEs once patched.
What’s Next?
This project was so much fun to work on, and it was extremely rewarding. I was so happy to see such a large group of students engaged and involved in this test at different levels from just observing, to reporting and actually helping to identify vulnerabilities. It was a great experience and one of my favorite proejcts from my time at CCSO.
This project was also an amazing opportunity to get real world experience and recognition for our work. Everyone walked away from this project with exposure to the different components of an actual pentest in addition to a report and CVEs to show off the quality of the work.
I hope that future CCSO members continue this effort and work to find more opportunities to conduct security assessments both within and outside of PSU. It was beneficial for everyone involved, and really fun 😄
- Title: A Student-Run Pentest: CCSO X HAX
- Author: Liam Geyer
- Created at : 2025-07-27 00:00:00
- Updated at : 2025-12-14 15:17:56
- Link: https://lfgberg.org/2025/07/27/security/hax-pentest/
- License: This work is licensed under CC BY-NC-SA 4.0.
