🧙🛜 WarWandering: Pt 2
In my last warwalking post, I used a Raspberry Pi and some basic equipment to put together a warwalking rig. Created for one of my graduate courses, the goal of this project was to collect data on wireless networks and to create dashboards to visualize trends in the data. I wanted to be able to map out and identify potentially insecure networks and paint a picture of wireless security in the State College area.
Overview
In the last portion of the project, I setup the hardware and software needed to collect wireless data on the go with Kismet. I took it on several test drives around the State College area, and now have several Kismet database files with the resulting data. Kismet provides output in sqlite databases containing information on devices seen, handshakes captured, GPS data, and much more.
To get some understanding and meaningful visualization out of this we’ll be ingesting the data into the Elastic Stack. This will allow us to easily and quickly search through the data, and use it to create visualizations and graphs. Elastic can’t just read a Kismet database, but I found a tool from Chase Peterson’s 2020 BSides Idaho talk that we can build off to ingest Kismet database files into ELK.
Setting Up
Before we can get any Kismet data into ELK we’ll first need to deploy an instance of the Elastic Stack. There’s an extremely convenient Docker Compose project that will allow for a two-command Elastic deployment.
All that’s needed to get this running is to install Docker and Docker Compose, clone the repository, and run docker compose up setup & docker compose up -d. I found that this deployment was more than enough for this project, and it allowed for quick redeployments which came in handy during testing.
Ingesting Data
Now that we have an ELK deployment running, we can work on ingesting our wardriving data into Kismet. I Started by attempting to use the wawkelk script from the BSides talk I found, but it had some issues out of the box due to the use of dynamic fields within the generated Elastic documents. Additionally, it couldn’t process files in batches and would need to be re-run per Kismet file.
I solved these issues after making some modifications to the script - it can now ingest folders of Kismet files, and imports without reaching field limits. I also changed the data being imported to ensure that duplicate or uneeded data wasn’t being ingested. You can get the modified version of the script on my GitHub.
Using the script, we can import the all the data found warwalking into ELK. It’ll create a new index that we can then search against and create dashboards with.
Creating Dashboards
With our data ingested into ELK, we can start creating dashboards to visualize trends in the warwalking dataset. Kibana allows for the easy creation of charts, tables, and graphs which can be easily directed to show data from a specific time period.
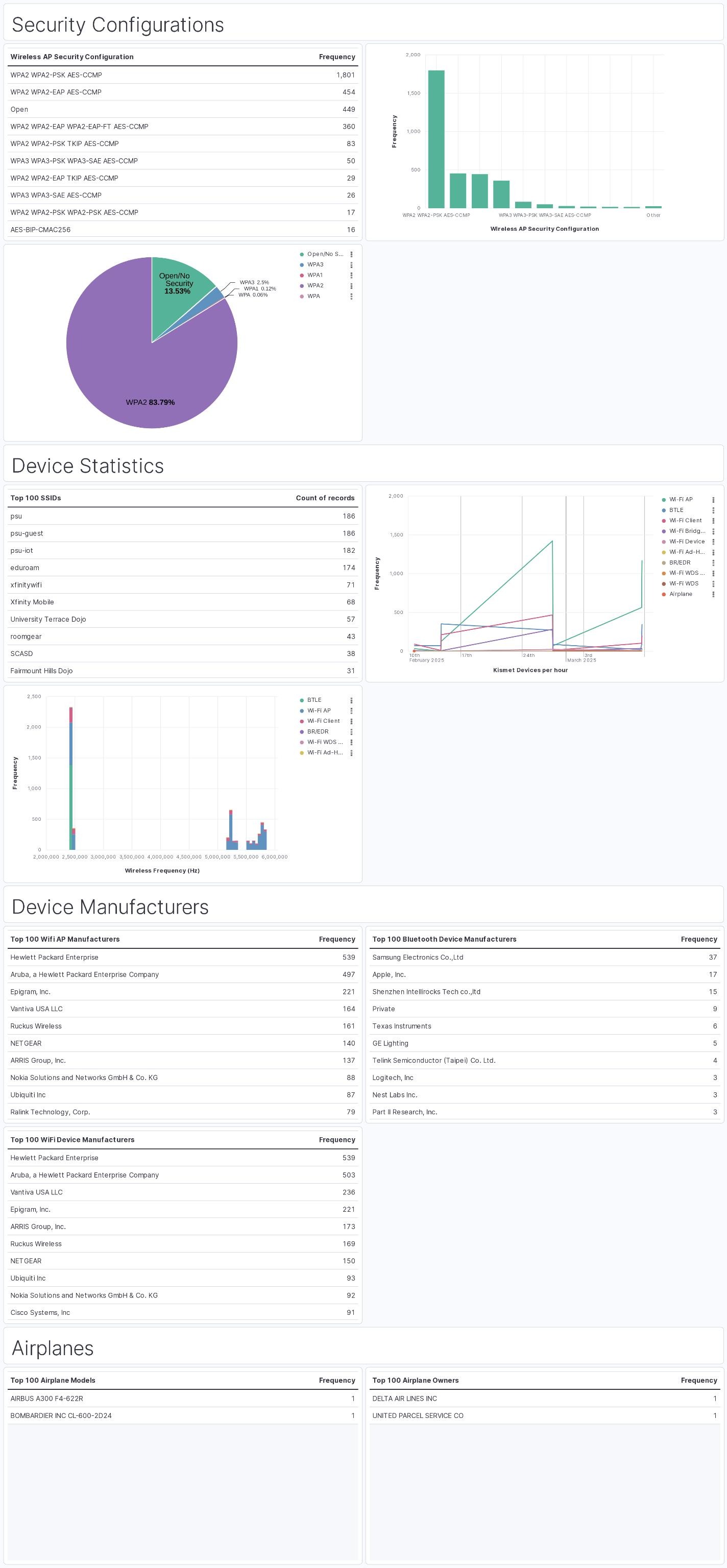
I created a proof-of-concept dashboard to show off some of the key trends and findings from my data collection including security configurations seen, devices seen over time, and device manufacturers. One of my favorite additions was a chart showing the wireless frequencies that detected devices were operating on.
Conclusions & Limitations
Overall, the collected data showed that very few detected networks were using the newest WPA3 Encryption (Only 2.5%), while a whopping 13.53% of networks were completely open. I attribute this at least partially to the area in which data was collected, as a lot of the captured networks were likely local businesses which commonly provide an open guest WiFi network. Although the data collection wasn’t thorough or large enough to draw any real conclusions it was a fun exercise in learning more about wireless security and wardriving.
In the future I’d like to write a tool to allow for the additional collection of information on WPA handshakes, which can be cracked to determine the password for a wireless network. Kismet will passively capture WPA handshakes and can provide a PCAP file for further processing. I’d like to be able to get anonmyized statistcs on crackable WiFi passwords by automating the process of removing SSIDs from their associated handshakes/hashes and attempting to crack the passwords.
- Title: 🧙🛜 WarWandering: Pt 2
- Author: Liam Geyer
- Created at : 2025-07-06 00:00:00
- Updated at : 2025-12-14 15:17:56
- Link: https://lfgberg.org/2025/07/06/security/warwandering-2/
- License: This work is licensed under CC BY-NC-SA 4.0.
